note the name of the backup file you got initially. Search on ways to exploit that popular service, especially on which exploit methods that can use those two files you split out from the .p** file.
Rooted!!
Good Windows machine for sure with good refreshers…at least for me. Kudos to @ctrlzero
Have root something to do with powershell? s**_****** doesn’t have admin rights and it cannot install missing powershell module for LAPS. I have some trouble with crackmapexec and I didn’t find passwords for other accounts. Can someone give me some direction?
From what you are saying, you are on your way there. I can only say to forget about crackmapexec and similar stuff. Think about what you were thinking about through your local enumeration, before you moved to the access you are relying on right now. If you enumerated that first access (yeah i’m trying to be slightly vague), repeat the process…you don’t need admin rights if you know what I mean.
Well, yes, you’re very vague. Maybe you’re telling a story. ![]()
hey, I tried to! ![]()
DM me if anything.
I got all the usernames with MSF6 sc#####/smb/smb_########
Admi######
G####
krb###
and more usernames im trying crackmapexec with rockyou.txt and no luck
and no luck loging as Guest
finally… root
wow, brain totally scrambled, lots learned, respect to @ctrlzero
Ok. I’ve found zip file, I extract and convert the p** to c** and k**. So, now I’m looking for user, because the only method that I’m thinking to use (e***-w****) needs user and password (even with t and y files). I’m trying to enumerate users through the basic like smb and ldap, but not success. If someone want to exchange tips feel free to dm me :)
i met it too,try with john --show
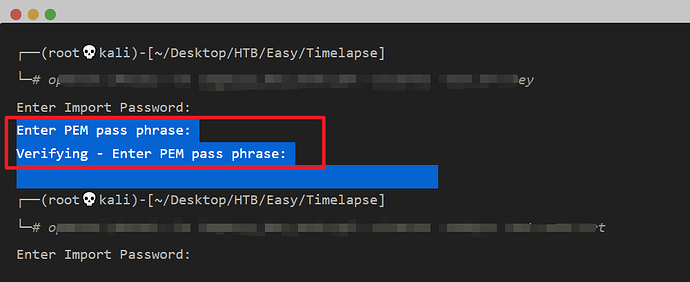
i met too, it asks me for PEM pass , and i don’t know what it is
Before to do what you want, with the same tool that you are trying to crack, search to alternatives that will help you with the initial extension of file you’ve found.
tks, i think i’ve find my mistake.
I should input the password by keyboard rather than cv ![]()
Need some help with priv esc. Got s**_******. I am not able to run SharpHound on the machine for some reason. My guesses are that there is a file somewhere or the account priv is exploitable. Hoping to get a hint of some sort here. ![]()
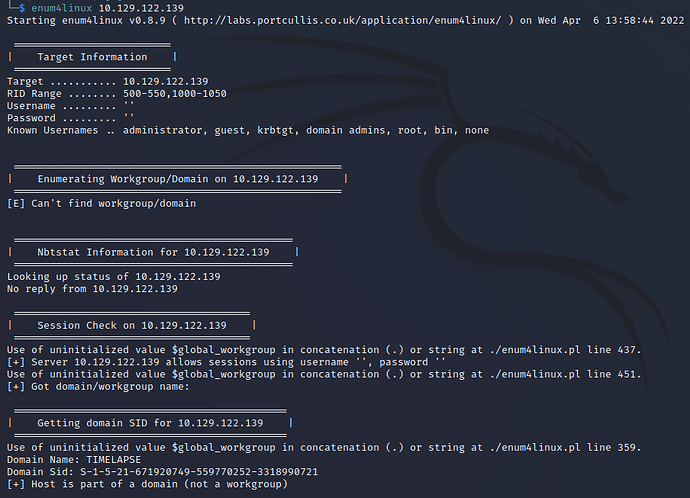
Any nudge on how to get foothold? never do windows machines…
it’s a more modern Windows OS, so your mileage may vary with enum4linux. However, just looking at your output, guest is enabled so a good first step would be to see what you can do with that. Couple that with port 445 being open and you can get the party started ![]() FWIW, I was able to complete the entire challenge using linux (Kali).
FWIW, I was able to complete the entire challenge using linux (Kali).
DM me if you get stuck.
are you logged in the S**_****** user or do you need creds for that user?
run ‘strings’ on the .p** file.