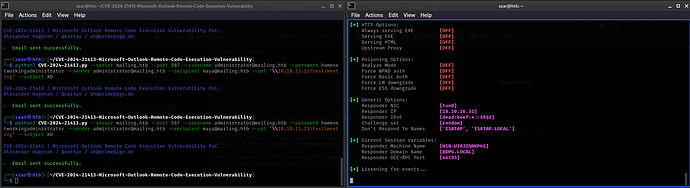
Hello could someone tell me why my responder didin’t catch anything??
I’m stuck in the same task. Checked and re-checked that everything is in place and it really looks like it is but still this hash doesn’t wanna come up…
Any help would be laaaaargely appreciated.
i think it’s just bugz out, try again.
did you manage to get this exploit working?? it still doesn’t work for me
Yes i did and i advice you to move on lol.
It took 2 days, many resets and a script that was sending the exploit every 20 seconds.
Also i got it just when i changed the url param from this
–url “\\10.10.10.10\wollabubbal”
to this
–url “\10.10.10.10\wollabubbal”
i don’t know if this is related or not but i got the hash
once this way and it didn’t come up anymore with the next tries and same command.
Once in the machine connection wasn’t stable, couldn’t even ping it for minutes.
So i took the user’s flag and called it a day.
That machine is def broken.
Ok, thx for advice i will try when i come back home .
User: As others have said, quite a disconnected story. You have to pay attention to the recent RCE that is related to the title. Some LFI cheatsheet will land you the pre-requisite of foothold for the CVE. If you are not getting an expected result, try emailing yourself to check the parameters. Still doesn’t work? Reset. This worked for me.
Root: Reset right off the bat, I am not joking, I was scratching my head off. Also pay attention to the spellings, OS locale affects SOMETHING.
did you get it?
you did resolve? im stuck in same task
it’s little hard to login with creds with thunderbird. I tried atleast 20 times to get 1 success after restarting and resetting the machine. Don’t know what the main problem is.
Any help???
@Preciouskavi
Best option in such times is to wait until the machine can work on ease
(maybe try on EU-VPN after midnight)
Other than that it will be dropping a lot of packets making the work harder.