I am currently trying to get a reverse shell in the Shells & payloads (Live engagement section 2) section of HTB academy, currently I see that the blog is vulnerable to this LFI Lightweight facebook-styled blog 1.3 - Remote Code Execution (RCE) (Authenticated) (Metasploit) - PHP webapps Exploit however the machine from which I am running the payload does not have the metasploit module and I have not managed to clearly understand the code in Ruby, I am a novice, I appreciate if someone can give me a hand.
Hey, this helped me “Importing Exploit-DB Exploits into Metasploit in Kali Linux for Offline Access”
After you do this, set the exploit path manually. I couldn’t find it with search.
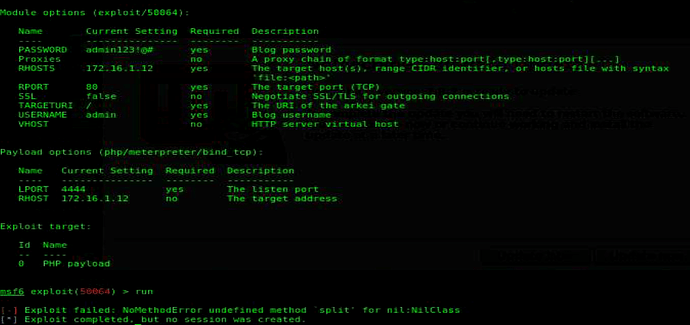
in metasploit I try with “use 50064.rb”… msf charge the exploit (Using configured payload php/meterpreter/bind_tcp ), then I put the RHOST,USERNAME(admin) and PASSWORD(admin123!@#) and run the exploit..but appears this messege: “Exploit failed: NoMethodError undefined method `split’ for nil:NilClass”
I don’t know how to solve it
I had the same problem.
For me, it was a bad parameter vhost.
Hi guys,
Did you solve the issue for that error?
Because i have the same problem.
Can you give me a tip, please?
hello, same problem to me anyone exploit problem ?
what do i have to do with the vhost?
do you managed to solve it?
Yes, you must put the URL on the VHOST
What is the login password? I can’t connect using the HTB_@cademy_stdnt! after connected to the foothold machine
try using on-screen keyboard to enter the password(HTB_@cademy_stdnt!)
Thanks for your suggestion
hew guys can anybody help me with the shell and payload live engagement i m one the last host-3. i found that was vulnerable to ms17-010 however when i try to get a meterpreter it keeps failing , i also found that i can upload aspx files directly to the host from the web so i thought of getting a webshell but still nothing
You can message me with details if you want
Thanks so much for your help. I think these three tasks are awful, nonmachine is really slow, awkward to use, the hints are not as helpful as they could be, the metasploit module has bad documentation… this module’s getting a 2 or a 1 star from me :). Great content but unnecessarily hard tasks and rubbish examples really drain your time!
Guys i need help..
maybe i doing something wrong but i cant use my PC (kali) VPN + NoMachine.
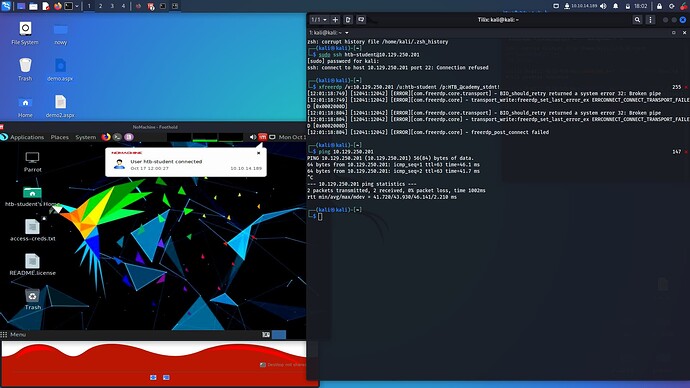
I spawned machine, got IP - ran NoMachine (it works) - and trying connect with ssh to it from my kali.
ssh: connect to host 10.129.183.214 port 22: Connection refused
I can ping and have access to targets (on nomachine) but one way to have it on my PC is - reverse shell on NoMachine(10.129.183.214) and then i got access to targets too (ping etc) but i have only terminal. I dont have WebBrowser and nothing more, do you have the same? Thats enough to do all in this section? I should do tunneling proxy in firefiox? If not, what i can do to have all options in this task?
I dont understand nomachine in this part, unless it’s specifically to make it difficult.. but this ssh should works
i loged in on NoMachine and finished path without VPN from my machine. Its was soo annoying…
Hi, I’m facing a problem as well, the 50064.rb exploit can’t be run by msfconsole. I get either this error:
uninitialized constant MetasploitModule::ExcellentRanking
or this one if I delete the ExcellentRanking line:
No classes were loaded from /pathtoexploit in the Msf::Plugin namespace
I could really use some help I’ve been stuck on this for a while and it’s starting to get on my nerves.
50064.rb shouldn’t have to be edited. You sure it’s in the right path?
Hi all, I’m getting extremely frustrated with this live engagement. From pwnbox I am unable to rdp to the foothold. From my vm + vpn I am unable to ssh to foothold (connection refused), and if I’m lucky enough to be able to connect to the foothold machine from my vm via xfreerdp, it’s not connected to the target network so I can’t even ping the target machines! What is going on!? Wasted a whole day just trying get on the network!!! Has anyone else had issues like this?