Hi, I’m currnetly trying to do the question “Connect to the target and perform a Kerberoasting attack. What is the password for the svc-iam user?”
I’ve connected to the Windows machines, ran Rubeus, created the SPN with the 3 users in.
I’m having isseus trying to crack this with hashcat.
Ive copied the content of the SPN file to the kali machine and tried running
hashcat -m 13100 -a 0 spn.txt passwords.txt --outfile=“cracked.txt”
and got: “passwords.txt: No such file or directory”
i found from the hints i need use SecLists/Passwords/Leaked-Databases/rockyou.txt so tried:
hashcat -m 13100 -a 0 spn.txt /usr/share/SecLists/Passwords/Leaked-Databases/rockyou.txt --outfile=“cracked.txt”
it started to run and ends with:
Hash ‘spn.txt’: Salt-length exception
No hashes loaded.
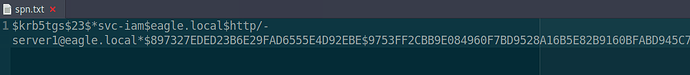
I edited the spn.txt with Pluma and removed the content for Administrator and webservice so i was just left with:
the SPN is ending 0DE51
but i still get the same Hash ‘spn.txt’: Salt-length exception.
I dont know what I’m doing wrong.
Not looking for answer to what the password is, but for what I’ve done wrong. Please help…