Hello all, when doing the lab, I am able to find bonni’s password and auth to the DC1 server does work as expected. When logging into DC1 and looking at the events in event viewer, I am unable to get a 4771 generated to answer the last question. Any suggestions? Thanks.
I have the same problem , you solve it?
still was unable to get the 4771 generated so just looked up the user’s sid with the “wmic useraccount” command. Hope that helps!
But… for example you take the wmic useraccount with which event ID? 4771 no right?
Yea I couldn’t get the 4771 event ID generated when purposely failing to Auth with the Bonni user. So I just ran the wmic useraccount command on the windows box and found Bonni’s SID. You get what I’m saying? Lol sorry if I suck at explaining things.
can you help me please i’m totally lost in this one, i don’t even get what even is that server? how to reach it and whats should i do with the found password? or is it irrelevant to the second question? any hint would be amazing! Thanks!
Is there a user called “webservice”? or how should I start the search? Anyone can drop a hint? Thanks in advance!
I am stuck on the second question for GPP Passwords.
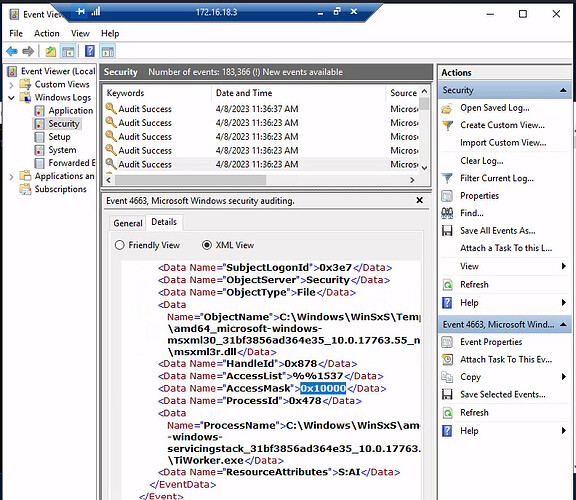
What is the Access Mask of the generated events?
The hint says to look for event ID = 4663.
I am getting the answer to the first question.
I then connect to the 172,16.18.3 machine and open the eventt viewer. Look for event 4663 under the security log and I get the following for access mask.
AccessMask 0x1
I then submit 0x1 as the answer but that is not correct.
Does anybody have any hints how to solve it?
Thanks
Overall, one needs to connect to the 172.16.18.3 machine.
I used remote desktop.
On the 10.129.x,y machine open a command shell.
From the command shell run mstsc.exe.
That opens the remote desktop GUI.
Enter the IP of the target machine and also user=htb-student.
It then asks for the password. Enter the given password. Accept the certifiate warning and then you get connected to the 172.16.18.3 machine as user htb-student.
Hope this helps.
Thanks man, I am getting back on track.
In case you didn’t solve it yet, there are multiple events with EventID 4663, take a look at the other one… ![]()
Hi!
Did everyone manage to use the script from this task?
It feels like he’s NOT a worker))))
I solved the problem by simply selecting all the “properties” by user.
But I would like to do it through a script.
wmic useraccount where name=‘bonni’ get name,sid
open cmd prompt and run wmic , it will come out
Hi - the sid given by that command - ending 3102, does not work. Any ideas much appreciated
Are you sure you entered the full SID without formatting errors (no leading/trailing characters etc)? You can find the typical SID format e.g. in these microsoft docs.
If that fails, try doing the task as intended by checking the log entries as suggested in the hint.
hello danny, from experience , any time you copy and paste any hash, or characters, or numbers or dash, or space, make sure no space and retype dashes and underscores…
You can start your own Internet Radio Station in minutes for FREE using the AZ-StreamingServer.com Platform.
Could use some help with the script for this.
I cannot get the script to work. I have set priveleges for powershell with -
Set-ExecutionPolicy Bypass -Scope Process
From here, put the provided script code in a text file and saved as .ps1
Running the file ( .\SearchUser.ps1 -Terms pass ) provides no output.
Just goes straight to another blank command prompt.
Currently unable to get the initial password while no scripts are able to run.
This worked -
powershell.exe -executionpolicy unrestricted
Randomly tried this script I found in the \highwaytohell folder.
.\SearchUser.ps1
This did the trick and was able to go on with the other questions. This wasnt explained in the module or question guidance. The method described in the module doesnt work