I am having a lot of issues with this one, not sure if the target is properly set up or I’m just stupid.
Spoilers below if you haven’t done this yet:
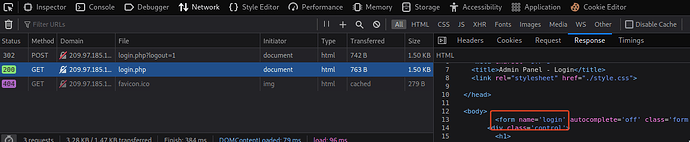
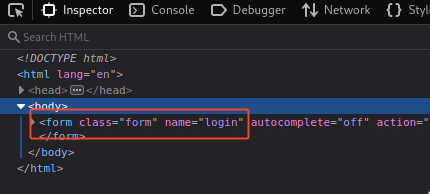
I’ve identified the path to be login.php, and I have proxied the data through burp suite to find the login parameters to use. I have looked at the source code of the login page to find a fail string to use:
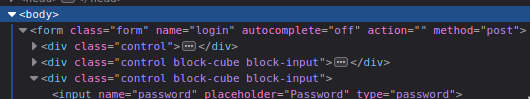
What I’ve come up with is this
"/login.php:username=^USER^&password=^PASS^:F=<form class='form' name='login'"
I get password matches for the user admin, but none of them work to sign in with. I have tried running hydra with and without -f, and I get a total of 16 passwords without that flag and I tried them all and none work, I simply get redirected to the login page each time.
I am trying to sign in through the form view, not the basic auth that you get if you omit /login.php.
Any hint on what I’m doing wrong would be greatly appreciated.