Hi, today we will try to find a solution using the knowledge that was explained in this module.
The next task reads as follows:
“Try running some of the web enumeration techniques you learned in this section on the server above, and use the info you get to get the flag”.
From what we read, the target can be the HTB VM target, and we will work with that. No further description.
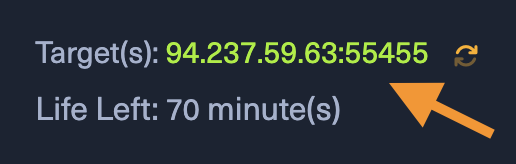
 Use the current available target IP address
Use the current available target IP address 
I did this on the platform, but it works the same on my local VM (Kali Linux).
- First we need to find the common.txt file. With this information we can run the
gobuster command:
find / -type f -name "common.txt" 2>/dev/null
… we take a result as given in the module: /usr/share/dirb/wordlists/common.txt
- Now we can run a
gobuster:
gobuster dir -u http://94.237.59.63:55455/ -w /usr/share/dirb/wordlists/common.txt
The given expression is a command-line instruction that utilizes the tool “gobuster” to perform a directory brute-force attack on a web server. Let’s break down the main parts of the expression:
gobuster dir
gobuster: This is the name of the tool being used. Gobuster is a popular tool for brute-forcing URLs and DNS subdomains.dir: This specifies the mode in which Gobuster is to be run. In this case, dir indicates that Gobuster is being used to brute-force directories and files on the web server.
-u http://94.237.59.63:55455/
-u: This flag specifies the URL of the target web server.http://94.237.59.63:55455/: This is the target URL. It includes the IP address (94.237.59.63), port (55455), and the root directory (/) of the web server being tested.
-w /usr/share/dirb/wordlists/common.txt
-w: This flag specifies the wordlist to be used for the brute-forcing attack./usr/share/dirb/wordlists/common.txt: This is the path to the wordlist file. The wordlist contains a list of common directory and file names that Gobuster will use to attempt to find valid directories and files on the target web server.
- The scan has completed successfully and identifies a different installation and specifically /robot.txt. Following the instructions of the “Web Enumeration” module, we execute the following command:
$ curl http://83.136.252.57:54378/robots.txt
 Use the current available target IP address
Use the current available target IP address 
or we can open it in a web browser.: 83.136.252.57:54378/robots.txt.
• As a result (terminal/browser) we get the next useful file - /admin-login-page.php 

 .
.
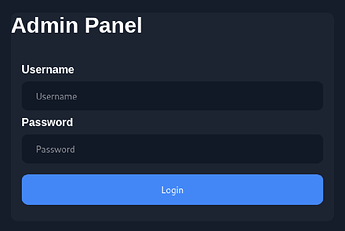
• Now let’s implement it in the browser only - 83.136.252.57:54378/admin-login-page.php
• Now we have such an interface, but what to do with a credential? Of course we should ask for help in the module again.
Source Code. As a suggestion, we could use
Ctrl + U.
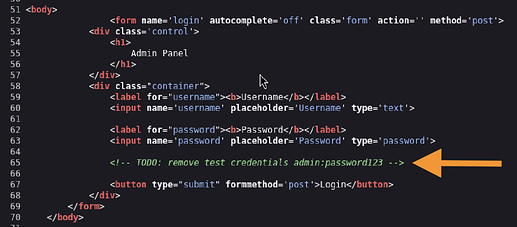
• For us was left interesting text

:
<! – TODO: remove test credentials admin:password123 →
• Enter
admin and
password123 and tap the [Login] button:
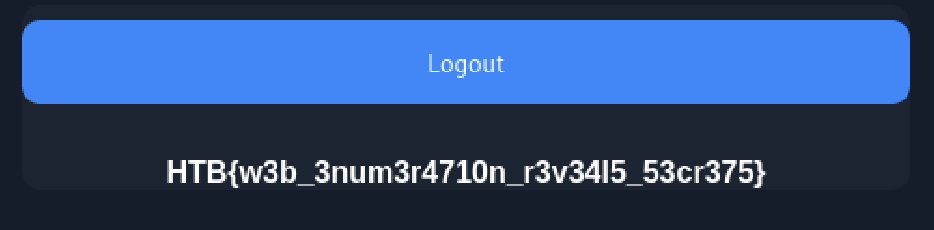
The answer on the screen. We did it 


 …
…
CONCLUSION:
My recommendation is to read with attention and several times. The key to success is practice, practice, practice. Repeat with the code in the module. If descriptions are not clear, search with googe or chat GPT.