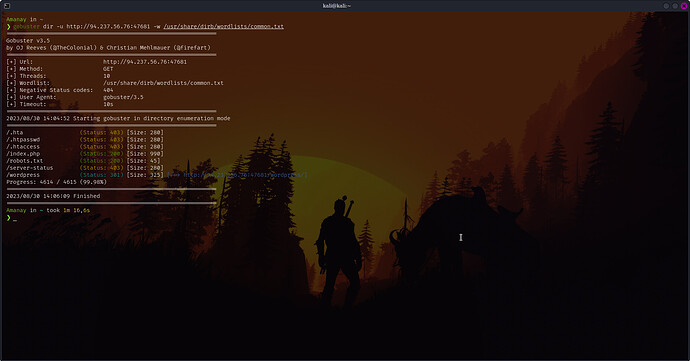
To solve the problem of the web enumeration section you have to use ( gobuster ) on the target IP that they give us:
❯ gobuster dir -u http://94.237.56.76:47681 -w /usr/share/dirb/wordlists/common.txt
Gobuster v3.5
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
/.hta--------------------- (Status: 403) [Size: 280]
/.htpasswd-------------(Status: 403) [Size: 280]
/.htaccess--------------(Status: 403) [Size: 280]
/index.php--------------(Status: 200) [Size: 990]
/robots.txt---------------(Status: 200) [Size: 45]
/server-status----------(Status: 403) [Size: 280]
Progress: 4614 / 4615 (99.98%)
2023/08/30 14:06:09 Finished
Next we place in the browser the IP with the access to the robots.txt file : http://94.237.56.76:47681/robots.txt
Will show us this : User-agent: * Disallow: /admin-login-page.php
Finally, it is enough to do a ( curl ) on the php file that we found previously : curl [ IP ]/admin-login-page.php, here the credentials will be displayed to log in to the php file that we found, when opening it from the browser it will show a login: [ IP ]/admin-login-page.php