Hi peeps, this might be one of the silliest modules in here and of course I’m stuck right with this one! Can somebody point me in the right direction pls?
.
After the xfreerdp connection I started searching inside the HTB-Academy folder finding a LOT of stuff.
Tried some stuff like a web shell in Tomcat, SMB connections with all emtpy shares.
Managed to get another connection to DEV01 via remmina but nothing interesting.
.
.
What am i missing? tia!
any luck figureing it out? I have a bunch of users and passwords at this point, some from kerbaroasting accounts etc.
no idea what to do from here.
Now that you have users and passwords, try them out on the machine you’re trying to get access to.
What ways can you perform remote authentication?
nope, I kept going on with other modules in the meanwhile, but yeah still have to complete this last exercise of this module ._.
Did you finish the module? I am don’t know what to do with all the password I found.
I’ll give a few hints and share some of my workflow there.
First, about the workflow. As you know very quickly, you’ll have to RDP from the ubuntu box, which makes the process slow and fragile. The creds for the Ubuntu box are working with SSH too. So I have configured this SSH connection with proxychain. Therefore I could RDP directly from my local VM with rdesktop (for some reason xfreerdp kept failing with proxychain).
Now, watch in the roasting findings. You should find a lead there. They seem to have stopped their tests in here… After that you should get some creds.
Now you should be able to jump to DC. Again proxychain RDP. Also a good Evil-WinRm, well configured with local scripts and binaries from Ubuntu box is even better.
For NTDS.DIT, you could also proxychain a netexec, which is fast and stable.
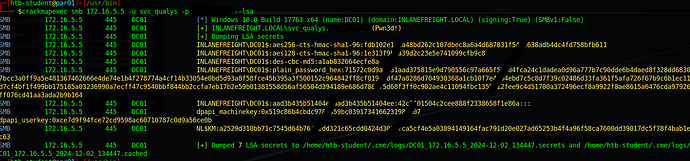
Hi, I don’t know if I’m missing something but I tried to find local admins of DC01. It seems that every member of the Domain Admin groups is Admin to DC01 (so svc_qualys, solarwindsmonitor etc) I got passwords of two of them and tried to dump lsa and sam hashes with crackmapexec. I got sam for Administrator but didn’t succeed to crack it or pth with it. I found 7 lsa secrets but none of them seems to belong to a domain user.
Am I doing somthing wrong or missing something (wrong user/method) or should I use lsa secrets but how ? Any help is appreciated ! Thanks
with that DC01$ account and hash you can perform a dcsync (impacket-secretsdump for example)
Yeah you right I can do this ! Thanks a lot !
Not the skills assessment but the notetaking part, i have tried so many different combos of the correct answer and it still wont say its correct. I know the answer I am just so frustrated that htb wont accept it and not sure what else it could be. I know this is super simple but i have not been
able to get past it. tyia!
Steve is learning about the tool that can make logging a session easier. He messages you for help mentioning that he would like to try to split the panes vertically. What do you tell him? (Answer format: [key] + [key] + [key], i.e., fill in the values for “key” and leave the brackets and + signs.)