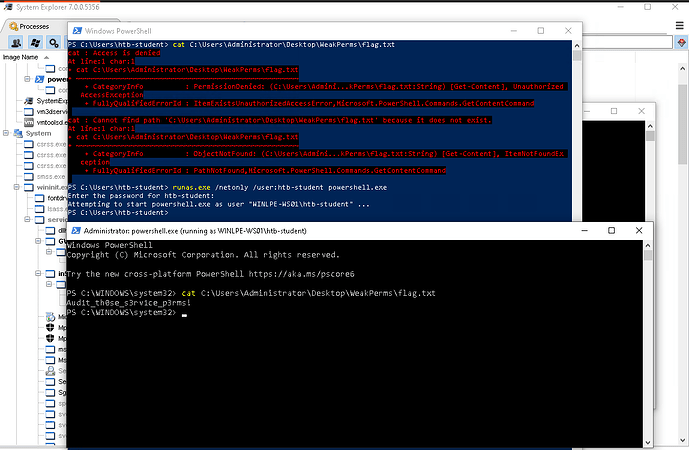
On a Windows privilege escalation room in academy, there is a section called Weak permissions. I managed to add my user to local administrators group, but still wasn’t able to read a flag. When you try to create an elevated powershell session, UAC asks for a password of a builtin Administrator user, which I don’t have, so this was not the option for me. For some reason, I thought about running runas.exe, and when I ran it with /netonly switch, seems like I was given an elevated terminal in which I could read a flag and also do high privileged actions like adding a new registry. This part confused me so much because it seemed like I bypassed UAC with just running runas.exe. I don’t know how exactly UAC interacts with other applications, so I wish someone will make things clear for me.