Hi guys.
I want to help you solve the problem with the Kali machine.
I myself have encountered this problem many times, but every time the task arose to attack a virtual server from my Kali machine, I always put off decisions for later, because I could not decide quickly.
If you are using the pwnbox virtual machine, then things are much simpler. You simply prescribe ip not of the network interface, but of the vpn connection. As has been written here many times.
But what if you are using your local Kali machine.
First, I would like you to think about how does your Kali machine know the route through the VPN tunnel?
Not like. You need a route from your kali machine to the attacked pwnbox server through a vpn tunnel.
The easiest way is to set up an open VPN on your Kali machine.
This can be done very quickly with the command
sudo apt-get update
sudo apt-get install openvpn network-manager
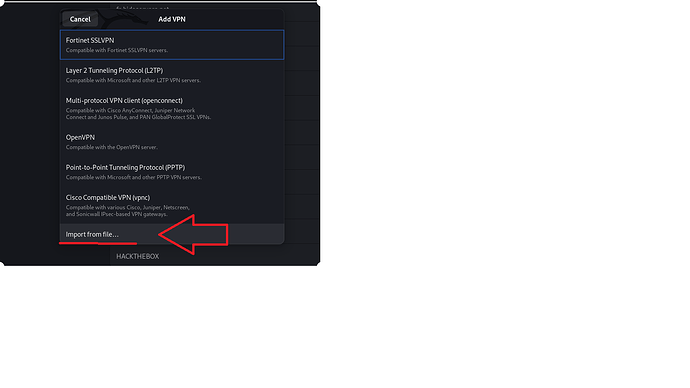
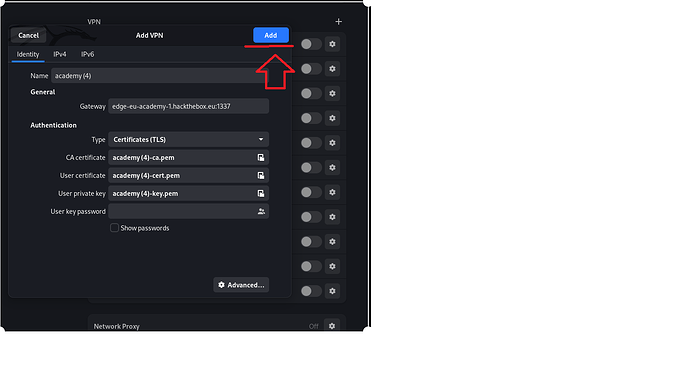
After that, you download the configuration file and create a new VPN interface in the settings of the Kali machine, where you import the configuration file without specifying a login and password!
That’s it - now you start a new VPN and everything should work.
When setting up the shell, you specify the VPN connection ip !!! instead of ip of your network interface!!!
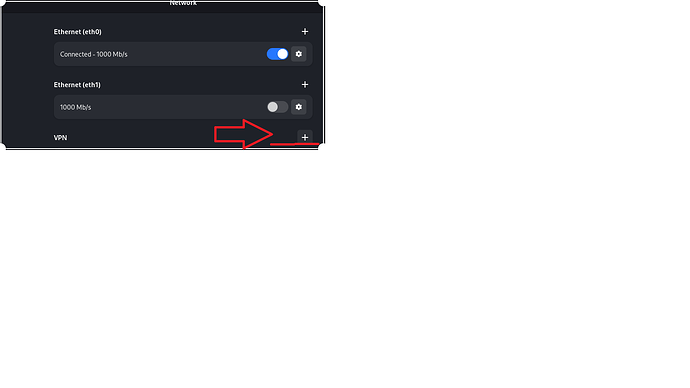
Be sure to make sure that you have 2 interfaces enabled, 1 - your network interface for Internet access, and 1 new VPN interface for connecting to the pwnbox network.
Good luck.
Create a VPN connection
Sorry for the screenshots in this resolution. did it quickly.
1 Like