I will keep checking back periodically and so if you get stuck or need some more nudges I am happy to help.
I would recommend the following two step approach:
- Do large nmap scans just to find out what is out there
- They mentioned the use of IDS/IPS so using some evasion techniques may yield more findings
- investigate the found ports using previously taught approaches
- more targeted nmap commands or banner grabbing, again hide from ids/ips
As an extra nudge from some good advice posted earlier:
Discovering the service and port is one thing, but there’s a technique that is given in the reading section Firewall and IDS/IPS Evasion that should help you connect the dots.
Took me one day and owned it eventually.
The tutorial has gone over everything needed. Just a small thing: time is our friend. Did not realize that…
@Middle_aged, thanks for the little push to go reread that section and the reminder to breathe. I was right there, but just got into that headspace where you sling commands at the server hoping something works. What I needed is even in my notes haha! Thanks again.
-onthesauce
gracias , me ayudo mucho lo que escribistes , pude entender mejor las cosas
this thread helped me, thanks alot.
I stumbled across the answer by mistake not even following the Hack the Box guide.
I came across it using nmap documentation for “dns-nsid”. You will find they use -sSU, and I used -T5 for this scan.
Then UDP appears in your results and you will be able to continue from there. looks like port 53 udp is interesting.
i know where i wrong, this ans need two step, step1:find the open port (big very much) step2:exchage tools to build connect with that port ,you will get the ans
I wasn’t totally sure what this problem was asking, so, if you feel the same, I hope this hint helps: try scanning every port on the host and investigate the open ones, esp those with higher numbers. I went down a rabbit hole probing port 53, but you’re looking for another HTB{} flag stored in the version banner of a service not explored in previous problems.
I also found the “Firewall and IDS/IPS Evasion” section helpful once I discovered the port to investigate.
just find the port you need and use sudo with netcup (without sudo it doesn’t work)
The trick for me was using Sudo.
This is the line I used to get the Flag.
sudo nc -nv -p 53 IP 50000
Hey still stuck on this even with sudo, returned this error:
sudo ncat --source-port 53 10.129.207.170 50000
[sudo] password for kali:
libnsock mksock_bind_addr(): Bind to 0.0.0.0:53 failed (IOD #1): Address already in use (98)
Ncat: TIMEOUT.
been stuck for almost a week, anyhelp appreciated
You are missing some parameters from what is included in the example in the academy materials “-nv” which might be important. look up what -n does
I tried everything here and couldn’t find the flag, it wasn’t until reading the forum that I discovered the port in question and yet I have no idea how I could find it as the VM and target have a limited lifespan and scanning all ports by UDP is very, very slow, even on -T5. How did anybody find the correct port by scanning with -p- in time!?
hello,
first find the port state, after that you can use simple command to find the “flag” service version
You do not need more than this to get your flag “sudo nc -nv -p 53 IP 50000”
something is wrong i cant get results from nmap because it takes alot of time dont know if due to lag. i change vpn file a still takes alot.
Based on DNS Proxying:
nmap <targetIp> -sS -Pn -n --disable-arp-ping --source-port 53 -v
now, you check the port 50000 with:
nmap <targetIp> -p50000 -sS -Pn -n --disable-arp-ping --source-port 53 -v
At this point, you figure out that now the port 50000 is open through port 53, so use Ncat:
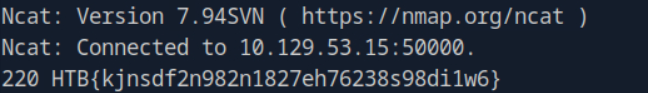
ncat -nv --source-port 53 <targetIp> 50000
I’ve just done this module and I ended up having tho rely on the comments here despite knowing the process I needed to follow already from reading the pages in the module.
Whenever I scanned using nmap, the result would ony come up with 2 ports showing open, and nothing else. even when I scanned port ranges 49500-50500 specifically, incase port 50000 hadn’t been captured in the top 1000 ports, still nothing showed up.
But when I scanned port 50000 alone it came up at filtered.
Can anyone help me with why it wouldn’t have been showing up in the initial scans?
I already had a search online about this, but I couldn’t find a satisfying answer.