I understand that there is another topic about this, but the comments got well off-topic with seemingly no resolution.
Question: Now our client wants to know if it is possible to find out the version of the running services. Submit the version of the service our client was talking about as the answer.
Steps I have taken are this command: ```
this gave me the new port that the question references. I then attempted ncat but I keep getting this error: libnsock mksock_bind_addr(): Bind to 0.0.0.0: failed (IOD #1)
I googled this to find that the issue is supposedly that PWN Box is running the DNS service systemd-resolved which I did find by using the find command at /usr/lib/systemd/system/systemd-resolved.service in the PWNBox.
I then used the command: sudo systemctl stop systemd-resolved
This did not change my ncat error. I also tried starting the service and then stopping it again.
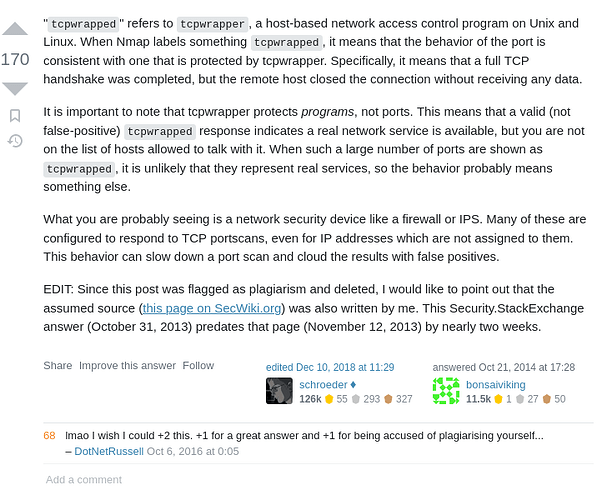
Any help would be greatly appreciated since many users were finding the answer with the same steps as me.