Fellow Hackers,
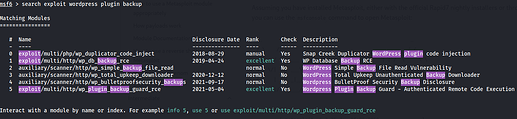
I am currently trying to solve this exercise. I am at the point where I need to decide what exploit needs to be used for this scenario. I have looked at the hint provided and it suggests looking for plugin exploits. Upon searching for exploits on Metasploit, I see exploits ranging from Remote code execution (RCE) to (Backup file Read Vuln).
The issue I ran into here is that I had no idea where this flag would be to actually use the appropriate exploit. After going through solutions from other users. It seems that they utilised a Backup File Read Vulnerability to download the flag. There seems to be a knowledge gap that I am having here. Please advice on how can I teach myself to match the objective(location of flag) with the appropriate exploit.
Now I am guessing that, in the exam no hints will be provided. Pentesters are required to figure out which exploit suits works best for the given objective. Would love to know how do you use do it.
Thanks