Do you use the tool dnsenum for solve this question? Or what are you did so far to solve this question? To know how help you or know what are you doing wrong.
Hey, would love to know how some came to an answer? I got the answer finally, too embarrassed to share how much time it took me tho…
I used the automated method and went through the list of sub domains from initial dig on domain…But again, took me hours …was something fierce tbh…very frustrating.
I’ve noticed some mentioning not needing to brute force but can dig way out…Once I solved, I tried to explore if dig was possible, but was not for me…Would love more insight from anyone.
I hope I don’t spoiler.
DNS Server: 10.129.138.203
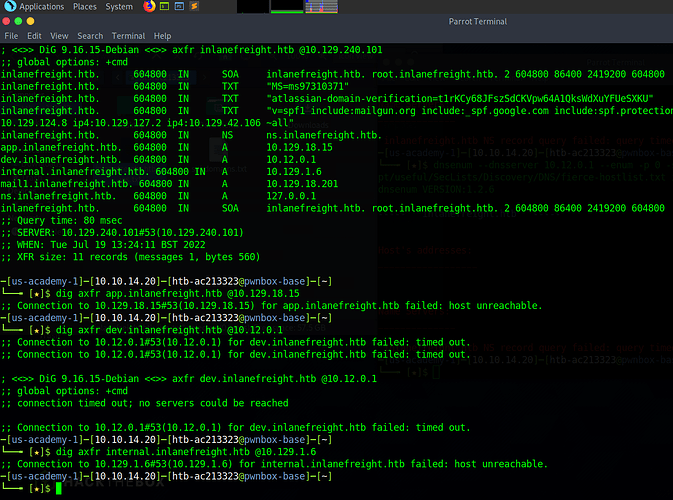
Start with axfr of inlanefreight.htb, it’s work:
app.inlanefreight.htb. 604800 IN A 10.129.18.15
- axfr don’t work
dev.inlanefreight.htb. 604800 IN A 10.12.0.1
- axfr don’t work
mail1.inlanefreight.htb. 604800 IN A 10.129.18.201
- axfr don’t work
ns.inlanefreight.htb. 604800 IN A 127.0.0.1
- axfr don’t work
internal.inlanefreight.htb. 604800 IN A 10.129.1.6
- axfr work
dc1.internal.inlanefreight.htb. 604800 IN A 10.129.34.16
dc2.internal.inlanefreight.htb. 604800 IN A 10.129.34.11
mail1.internal.inlanefreight.htb. 604800 IN A 10.129.18.200
ns.internal.inlanefreight.htb. 604800 IN A 127.0.0.1
vpn.internal.inlanefreight.htb. 604800 IN A 10.129.1.6
ws1.internal.inlanefreight.htb. 604800 IN A 10.129.1.34
ws2.internal.inlanefreight.htb. 604800 IN A 10.129.1.35
wsus.internal.inlanefreight.htb. 604800 IN A 10.129.18.2
I try for all domaine with, all wordlist, nothing to do. ![]()
dig any $sub.inlanefreight.htb @10.129.138.203 with all wordlist → same result than axfr.
dig any $sub.[app/dev/mail1/internal].inlanefreight.htb @10.129.138.203 with all wordlist. → don’t work.
Also try this, don’t work.
for sub in $(cat /opt/useful/SecLists/Discovery/DNS/subdomains-top1million-110000.txt);do dig $sub.inlanefreight.htb @10.129.138.203 | grep -v ‘;|SOA’ | sed -r ‘/^\s*$/d’ | grep $sub | tee -a subdomains.txt;done
dnsenum --dnsserver 10.129.138.203 --enum -p 0 -s 0 -o subdomains.txt -f /opt/useful/SecLists/Discovery/DNS/subdomains-top1million-110000.txt inlanefreight.htb
I finally found it thanks to your help. Once found, it seems easy… ^^
Thank you.
I am still having issues with this.
Can somebody give me another clue?
what did you try?
feel free to dm me
I finished the module successfully. Thanks
I was still struggling on this module even with the hints above. For anyone else still struggling with this specific question, like others have mentioned: start by doing a dig Zone Transfer command on the main domain using the target machine’s IP as the DNS server. Then record all the subdomains you get back. Then use dig to try and Zone Transfer on those subdomains (app.inlanefreight.htb, internal.inlanefreight.htb, dev.inlanefreight.htb, etc.) and record any that you cannot get records for.
Finally, use either the bash script or the DNSEnum tool to brute force the subdomains you couldn’t get records for using a very “fierce” wordlist. Good luck and hope you learn something new like I did! ![]()
hi geekecom can u help me with that last question
Thank you camlen92. Thanks to your comment “fierce” I realized that I was using an incorrect wordlist and just that wordlist called “fierce???.txt” in SecLists is the good one.
I was helped by the first image that appears in the theory where I understood that an axfr applied to a domain allows you to find out the subdomains of that domain and an axfr applied to a subdomain allows you to find out the hosts.
I was doing everything right except choosing the correct wordlist. The steps to follow are the same as you comment and the ones I followed.
The exercise is entertaining, but I think HTB Academy should specify the wordlist to use because I lost a lot of time in this exercise just for not choosing the right list of words. By the way I used the DNSenum tool.
I thought there where spoilers on this forum, I took the clues and figured it out 15 minutes later.
am i supposed to be getting host unreachable and time out errors for every subdomain? i have buteforced with bash script and dnsenum but no dice
I don’t think so. You probably need to reset the target
Can someone point me in the right direction for that last question?
I tried zone transfers on all the subdomains for inlanefreight.htb seems like internal.inlanefreight.htb is the only subdomain I found that responds to the transfer. I found a bunch more subdomains in internal.inlanefreight.htb and tried both zone transfer and brute force (dnsenum) with the fierce wordlist. I cannot seem to find anything ending in .203 IP… I also tried brute force on all the subdomains from inlanefreight.htb as well.
There are zones that do not allow zone transfers from anyone.
You must then bruteforce these zones. Your list is right.
If you are still stuck, write me a DM.
@CrazyHorse302, focus your brute force efforts on zones that are not allowing transfers. As I mentioned above, be “fierce” about it when using your wordlists ![]()
Lastly, don’t get discouraged! Pentesting is all about learning and working on your patience.
Good luck!
Got it! thanks for the hints, I went back over the suggestions in a more methodical way this time and found it pretty quick.
Just solved this.
When you dig or run the dnsenum tool use the target ip dont use the ip’s for the domains that show up in your dig. when i read the hints others left that’s what i thought others where doing, it set me back alot
ilan20 tip and PayloadBunny tips got the solution for me
Nice hint!