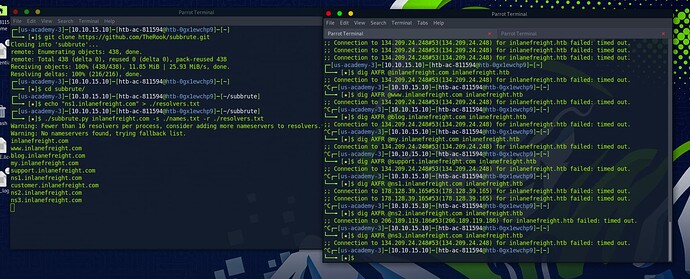
It is Very Simple Lab, the main trick is on the Zone Transferring process and Brute forcing the subdomains, then on some subdomain when u do Zone Transfer u will get the Flag. for the Bruteforce i used subbrute and for the zone transfer i used host
I have done I am stuck ACS m**in user connect to mail server to get flag from email have you done that
WARNING: I will be spoiling a part of this lab
I’ve associated the given IP and domain name, got the subdomains and still not able to determine which one is correct for the zone transfer. Any help would be greatly appreciated!
Any hint? I’m doing the same thing but not coming up with anything
Remember to use the query in this format:
dig DNS @IP
You are not looking up the right subdomain
i’m struggling from last 2 weeks and not able to solve. Any hint how to solve this lab?
dm me
Guys please help me, I really don’t know what I’m doing wrong. Two days in here I want to believe there’s something wrong with my pwnbox. I’ve tried axfr with every domain, subbrute works normally, yet nothing
Hey Daniel ![]() Couple things for you my man:
Couple things for you my man:
During your subbrute stage, keep an eye on the domain you are brute forcing. Are you sure you should be doing inlanefreight.com? It might seem confusing since many of the examples have inlanefreight.com as the domain, but look at the question being asked and tweak that domain accordingly. Also your resolvers file entry doesn’t need a subdomain, hint hint. You’ll discover a unique subdomain this way when running the command. And lastly when you are ready to do your last dig AXFR command, be aware of which domain/subdomain you are putting in sequence in the command. The module makes it look like anything with a subdomain goes in the @ parameter but play around with this and you will get your answer.
This one is kind of a doozie but there aren’t many steps. Keep marching forward with confidence ![]()
Thank you so much, I got it ![]()
I couldnt do it. Any hint?
I just put in the /etc/hosts de subdomain, but nothing.
For anyone still confused you have to update the /etc/host file with the (ip) then ns1.inlanefreight.htb, after that use subbrute. Make sure the resolver.txt is updated correctly with inlanefreight.htb & do not use .com wait like 5-10 minutes for results. Finally use dig for zone transfer. DM me if you still can’t figure it out…
Adding the IP of the domain AND the address of the dns in /etc/hosts really saved me. Thanks !
Hey Ali88! It won’t work with the IP in the resolver.txt file? The host file is easy enough to adjust to - just wondering if you tried it that way too.
Use nano to edit the resolver.txt file & put inflanefteight.htb that should be the only thing in there.
I’m going to give your suggestion a try sometime today. I had dropped the IP address into the resolver file and was getting results but it was taking forever. It was working for a while but not finishing that way. You’re awesome! Thanks for the feedback.
This took me a really long time to solve but I was very close to the solution after about 15 minutes, I just didn’t realize it. If I had simply reversed the order of two dig entries, I’d have had it.
I went so long I thought pwnbox was broken. It wasn’t. It’s just a tricky question. They want you to learn about dig and subbrute, not just follow the instructions.
My hint: @inlanefreight.htb
Hi all. Looks like everyone is facing the same issue and I realised that there is no tools that help brute force zone transfer on subdomain. I’ve created a simple python tool that use dig axfr command to perform query on subdomain from a wordlist. Hope it helps everyone and really appreicate a star if that helped you!
Usage: python3 ZTBrute.py {domain} {IP} {wordlist}
Add inlanefreight.htb in /etc/hosts and resolvers.txt from subbrute.
In /etc/hosts, your line should look like this:
<IP> inlanefreight.htb
To be sure use you have the correct resolvers.txt, use in subbrute folder:
echo inlanefreight.htb > resolvers.txt (if you don’t have permission use sudo su to be root).
After you make sure everything is correct, go ahead for ./subbrute <DNS> , then
dig AXFR <DNS> <@IP>.