Hi Everyone! I’ve been learning and practicing Windows privilege escalation. I read writeups of Tally, Conceal & Jeeves. These machines are Windows 10 and have SeImpersonatePrivilege token enabled, but Juicypotato only works on Conceal. So how do we know exactly where to run JuicyPotato or RottenPotato. Is it based on Windows versions or something else? Any type of help would be appreciated. Thanks!!
When you say it didn’t work on 2 out of the 3, did you actually try it or do you just mean it wasn’t used by people in their write ups?
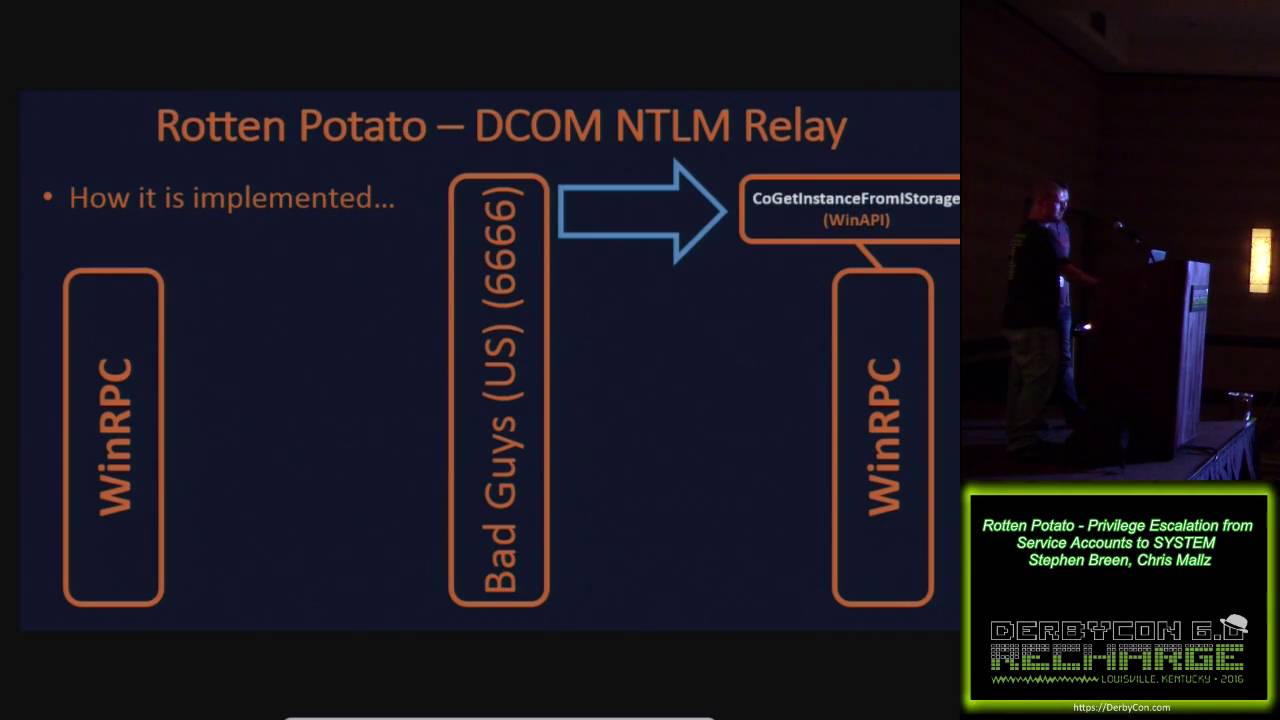
Also not sure if you’ve seen it already but there’s a detailed explanation of the way it works here
I tried Juicy Potato on Jeeves, it didn’t work. But Rottenpotato did
Oh right, I thought you were saying neither of them worked on Jeeves and Tally. My understanding was that JuicyPotato is the same as RottenPotato but just with more options (like choosing which DCOM service it calls and which port it uses). So that is odd.
How many different service CLSIDs did you try attack with JuicyPotato? I often have to try several before I get one that works. Perhaps you just didn’t try using the same CLSID that RottenPotato uses and that’s why Rotten worked but Juicy didn’t? I think Rotten uses one of the CLSIDs from the BITS service but not sure which one. You can find a list of all the CLSIDs here and you’ll see some of them do vary depending on OS: Windows CLSID | juicy-potato
This just came up again on Twitter and long story short: it turns out the technique JuicyPotato and RottenPotato use is no longer possible on Server 2019 or Windows 10.
More info here:
And in the twitter thread here:
https://twitter.com/ippsec/status/1258518781690703873
While I was looking into it I did find some new tools that use similar concepts (requiring you to have the right to impersonate users just like JuicyPotato) but with named pipes: GitHub - itm4n/PrintSpoofer: Abusing impersonation privileges through the "Printer Bug"