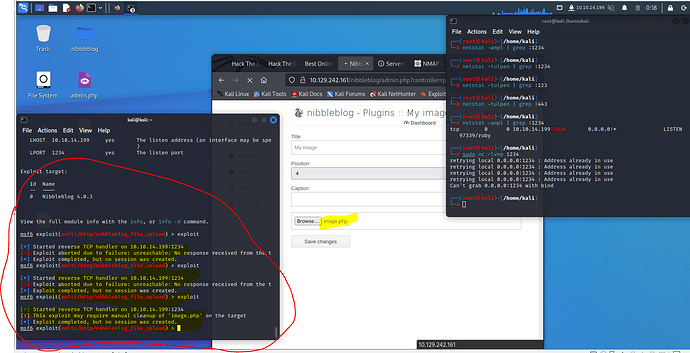
Everytime I try a metasploit exploit, it can’t seem to connect to my listener.
I have confimed I’m connected to HTB’s vpn. If I surf the tareget site using firefox, wireshark shows the IPs I’m using (mine and the targets) are correct.
When I run the exploit, I get this message:
-] Handler failed to bind to 10.10.14.82:4444:- -
[-] Handler failed to bind to 0.0.0.0:4444:- -
[-] 10.129.42.249:80 - Exploit failed [bad-config]: Rex::BindFailed The address is already in use or unavailable: (0.0.0.0:4444).
[*] Exploit completed, but no session was created.
strange, change the port by the warning it seems that there is already another process listening on port 4444
I figured it out. I didn’t realize I didn’t need to manually setup a listener when using metasploit exploits. My netcat listener was the conflict.
you are probably setting up your rhosts to the IP address of the machine you want to exploit, in addition, you will need to setup lhost to the IP address of the vpn gatway (you can find this on HTB portal where it shows you are connected to the VPN
I have done both manual and Metasploit msfconsle still not getting a reserve shell, pls what could i be doing wrong?
I’m having the same problem when I try to listen on my public IP. I did my port forwarding using a VPN service TorGuard and whenever I try to connect listen on the IP assigned by tor guard, it gives an error about not being able to bind on it. After using the ReverseListeningBindAddress and the ReverseListeningBindPort, I got some unexpected results like the one below: