Try to find ccache file and export it to KRB5CCNAME=… then use smbclient
try fpt and -t 48
Howdy folks. I’m hopelessly stuck on Password Reuse / Default Passwords. I’ve read the module, tried all the default mysql passwords, googled a bit, to no avail. I have successfully SSH’d in, but after much fishing around in there I’m at a loss. I’m hoping someone can share a massive breadcrumb so I can continue on the trail.
Hi. Would you mind telling me that which username list you used? Thank you
Did anybody solve that second optional exercise?
From Windows (MS01), export Julio’s ticket using Mimikatz or Rubeus. Convert the ticket to ccache and use it from Linux to connect to the C disk
I think I could use a nuge… Cause I’m currently running wild!
OK, got it. Don’t try to access DC01 from Kali. Go LINUX01!
I solved it, just used the hash of the previous module
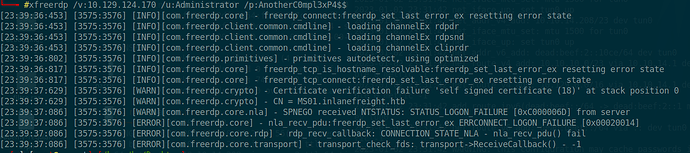
Someone can help me, i cant RDP to the Pass The Ticket From Windows Machine, I use the credentials that htb say but displays this error.
guys don’t wast your time. think like an attacker .
if you find a valid user and password then you can login and retrive all users in the system and update your users list ![]()
Note: valid user and pasword list are provided check resources
I’am stuck at Password Attacks Lab - Hard I have found the password of user D**** but it isn’t possible to rdp in. Also not possible to change user. do anyone have a hint for me?
I’ve use a cmd with runas /user: and found a vhd but i can not mount it
For anyone still busy with the Password Mutations task, one little bit of advice that I can share is when you generate the list, you can make it a bit smaller by doing : cat mutated.list | sort | uniq > new_mutated.list
This is common knowledge, but when I did some reading up on how to make the list shorter there was an article that said to use the -u flag with uniq and that ended up costing me hours since it removed duplicates all together and ended up removing the valid password from the list as well.
The valid password is in the mutated list, if you use the provided password list and rule set, it just takes some time to work through it. (Also using Hydra on pwnbox is quite a bit faster than on your host machine)
Im stuck in the easy attack lab.
After doing a nmap scan, both tcp and udp ports, I see ftp , ssh and dhcp services. I have tried to bruteforce both ftp and ssh with the credentials in the resources part of the module. I have also tried the root user with a mutated list of the passwords using the hashcat rules offered in the zip, and also the default nmap bruteforce list, but nothing worked.
Do anybody have a clue?
EDIT: Seems like using faster timings makes bruteforcers to not work properly. I reduced treads and I got the user and pass.
Hi guys,
I’m at this question: Check the /tmp directory and find Julio’s Kerberos ticket (ccache file). Import the ticket and read the contents of julio.txt from the domain share folder \DC01\julio.
I really don’t know what to do, can anyone help me? You can even dm me if you pref.
Thank you, I solved it because of the path found in the demonstration. But if we didn’t have that, how do we get to that ticket? Since it doesn’t even have the extension we were using with the find tool
Has anybody got crackmapexec working on the Pwnbox ?
I get dependency errors also when I build it from the source
Edit:
Managed to install it with these commands:
- python3 -m pip install pipx
- pipx ensurepath
- pipx install crackmapexec
Please Any one help me out :-
Use the LINUX01$ Kerberos ticket to read the flag found in \DC01\linux01. Submit the contents as your response (the flag starts with Us1nG_).
1. first connect to ssh to the target
2. then there are keytab files so use python tool to decrypt passwords
3. su to that user with pass we got
4. again same process but this time search carefully the keytab files are in crontab
5. change the env variable and query the smb
6. now we are in another user acc we can sudo su
7. now we are root search care fully for kerbros tickets we will find them in /root/.k*/**
then exit because I was stuck here from 2 days if any one get last flag please help me by just giving hints ![]()
did you manage to connect with rdp? I’m stuck with the same problem rn and kinda confused
EDIT: already got it, don’t know why this time had to be different
Hi all,
I’m currently stuck in the “Password Attack | Protected Files” section.
The task says “Use the cracked password of the user Kira and log in to the host […]” but I cannot find a password for Kira. Kira isn’t mentioned anywhere in this section and it feels like I’m supposed to reuse a password cracked in an earlier section of this module.
Could anyone please give me a hint as to where I can find the password for Kira’s account?
Thank you & best regards ![]()
hey, any hint on how did you get it?
Hi, did you solve it? I am stuck here too… I am in with kira but find nothing…thanks