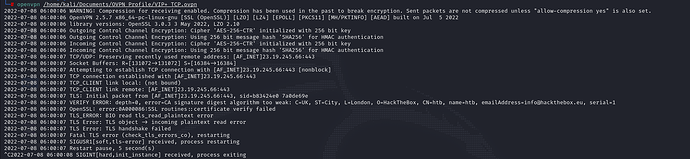
Hi! I was testing an active machine earlier this morning and then after upgrading packages, it seems things have broken. I am not 100% sure what exactly the issue is, although I suspected it was related to upgrading to OpenVPN 2.6.
I tried downgrading to OpenVPN 2.4 but that opened up an entirely different can of worms… Does anyone know of a solution by chance? Any ideas, thoughts or suggestions is greatly appreciated!
Note: I have also tried simple troubleshooting steps such as restarting the host as well as downloading multiple different .ovpn files from HTB
$ sudo openvpn lab_lnsomnia.ovpn
2022-06-23 17:31:10 WARNING: Compression for receiving enabled. Compression has been used in the past to break encryption. Sent packets are not compressed unless "allow-compression yes" is also set.
2022-06-23 17:31:10 DEPRECATED OPTION: --cipher set to 'AES-128-CBC' but missing in --data-ciphers (AES-256-GCM:AES-128-GCM:CHACHA20-POLY1305). OpenVPN ignores --cipher for cipher negotiations.
2022-06-23 17:31:10 Cannot find ovpn_dco netlink component: Object not found
2022-06-23 17:31:10 Note: Kernel support for ovpn-dco missing, disabling data channel offload.
2022-06-23 17:31:10 OpenVPN 2.6_git x86_64-pc-linux-gnu [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [PKCS11] [MH/PKTINFO] [AEAD] [DCO] built on May 30 2022
2022-06-23 17:31:10 library versions: OpenSSL 3.0.3 3 May 2022, LZO 2.10
2022-06-23 17:31:10 Outgoing Control Channel Authentication: Using 256 bit message hash 'SHA2-256' for HMAC authentication
2022-06-23 17:31:10 Incoming Control Channel Authentication: Using 256 bit message hash 'SHA2-256' for HMAC authentication
2022-06-23 17:31:10 TCP/UDP: Preserving recently used remote address: [AF_INET]23.19.245.66:1337
2022-06-23 17:31:10 Socket Buffers: R=[212992->212992] S=[212992->212992]
2022-06-23 17:31:10 Note: enable extended error passing on TCP/UDP socket failed (IPV6_RECVERR): Protocol not available (errno=92)
2022-06-23 17:31:10 UDP link local: (not bound)
2022-06-23 17:31:10 UDP link remote: [AF_INET]23.19.245.66:1337
2022-06-23 17:31:10 TLS: Initial packet from [AF_INET]23.19.245.66:1337, sid=9dd76651 d9d3ba31
2022-06-23 17:31:10 VERIFY OK: depth=1, C=UK, ST=City, L=London, O=HackTheBox, CN=HackTheBox CA, name=htb, [email protected]
2022-06-23 17:31:10 VERIFY KU OK
2022-06-23 17:31:10 Validating certificate extended key usage
2022-06-23 17:31:10 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
2022-06-23 17:31:10 VERIFY EKU OK
2022-06-23 17:31:10 VERIFY OK: depth=0, C=UK, ST=City, L=London, O=HackTheBox, CN=htb, name=htb, [email protected]
2022-06-23 17:31:10 WARNING: 'auth' is used inconsistently, local='auth SHA2-256', remote='auth SHA256'
2022-06-23 17:31:10 Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384, peer certificate: 2048 bit RSA, signature: RSA-SHA1
2022-06-23 17:31:10 [htb] Peer Connection Initiated with [AF_INET]23.19.245.66:1337
2022-06-23 17:31:10 PUSH: Received control message: 'PUSH_REPLY,route 10.10.10.0 255.255.254.0,route 10.129.0.0 255.255.0.0,route-ipv6 dead:beef::/64,tun-ipv6,route-gateway 10.10.14.1,topology subnet,ping 10,ping-restart 120,ifconfig-ipv6 dead:beef:2::1059/64 dead:beef:2::1,ifconfig 10.10.14.91 255.255.254.0,peer-id 2,cipher AES-128-CBC'
2022-06-23 17:31:10 net_route_v4_best_gw query: dst 0.0.0.0
2022-06-23 17:31:10 net_route_v4_best_gw result: via 10.0.2.2 dev eth0
2022-06-23 17:31:10 ROUTE_GATEWAY 10.0.2.2/255.255.255.0 IFACE=eth0 HWADDR=08:00:27:37:63:9a
2022-06-23 17:31:10 GDG6: remote_host_ipv6=n/a
2022-06-23 17:31:10 net_route_v6_best_gw query: dst ::
2022-06-23 17:31:10 sitnl_send: rtnl: generic error (-101): Network is unreachable
2022-06-23 17:31:10 ROUTE6: default_gateway=UNDEF
2022-06-23 17:31:10 TUN/TAP device tun0 opened
2022-06-23 17:31:10 net_iface_mtu_set: mtu 1500 for tun0
2022-06-23 17:31:10 net_iface_up: set tun0 up
2022-06-23 17:31:10 net_addr_v4_add: 10.10.14.91/23 dev tun0
2022-06-23 17:31:10 net_iface_mtu_set: mtu 1500 for tun0
2022-06-23 17:31:10 net_iface_up: set tun0 up
2022-06-23 17:31:10 net_addr_v6_add: dead:beef:2::1059/64 dev tun0
2022-06-23 17:31:10 net_route_v4_add: 10.10.10.0/23 via 10.10.14.1 dev [NULL] table 0 metric -1
2022-06-23 17:31:10 net_route_v4_add: 10.129.0.0/16 via 10.10.14.1 dev [NULL] table 0 metric -1
2022-06-23 17:31:10 add_route_ipv6(dead:beef::/64 -> dead:beef:2::1 metric -1) dev tun0
2022-06-23 17:31:10 net_route_v6_add: dead:beef::/64 via :: dev tun0 table 0 metric -1
2022-06-23 17:31:10 OPTIONS IMPORT: timers and/or timeouts modified
2022-06-23 17:31:10 OPTIONS IMPORT: --ifconfig/up options modified
2022-06-23 17:31:10 OPTIONS IMPORT: route options modified
2022-06-23 17:31:10 OPTIONS IMPORT: route-related options modified
2022-06-23 17:31:10 OPTIONS IMPORT: peer-id set
2022-06-23 17:31:10 OPTIONS IMPORT: data channel crypto options modified
2022-06-23 17:31:10 Error: negotiated cipher not allowed - AES-128-CBC not in AES-256-GCM:AES-128-GCM:CHACHA20-POLY1305
2022-06-23 17:31:10 OPTIONS ERROR: failed to import crypto options
2022-06-23 17:31:10 ERROR: Failed to finish option processing
2022-06-23 17:31:10 Failed to open tun/tap interface
2022-06-23 17:31:10 SIGUSR1[soft,process-push-msg-failed] received, process restarting
2022-06-23 17:31:10 Restart pause, 5 second(s)
2022-06-23 17:31:15 Outgoing Control Channel Authentication: Using 256 bit message hash 'SHA2-256' for HMAC authentication
2022-06-23 17:31:15 Incoming Control Channel Authentication: Using 256 bit message hash 'SHA2-256' for HMAC authentication
2022-06-23 17:31:15 TCP/UDP: Preserving recently used remote address: [AF_INET]23.19.245.66:1337
2022-06-23 17:31:15 Socket Buffers: R=[212992->212992] S=[212992->212992]
2022-06-23 17:31:15 Note: enable extended error passing on TCP/UDP socket failed (IPV6_RECVERR): Protocol not available (errno=92)
2022-06-23 17:31:15 UDP link local: (not bound)
2022-06-23 17:31:15 UDP link remote: [AF_INET]23.19.245.66:1337
2022-06-23 17:31:15 TLS: Initial packet from [AF_INET]23.19.245.66:1337, sid=7b482d64 6ba69081
2022-06-23 17:31:15 VERIFY OK: depth=1, C=UK, ST=City, L=London, O=HackTheBox, CN=HackTheBox CA, name=htb, [email protected]
2022-06-23 17:31:15 VERIFY KU OK
2022-06-23 17:31:15 Validating certificate extended key usage
2022-06-23 17:31:15 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
2022-06-23 17:31:15 VERIFY EKU OK
2022-06-23 17:31:15 VERIFY OK: depth=0, C=UK, ST=City, L=London, O=HackTheBox, CN=htb, name=htb, [email protected]
2022-06-23 17:31:15 WARNING: 'link-mtu' is used inconsistently, local='link-mtu 1573', remote='link-mtu 1570'
2022-06-23 17:31:15 WARNING: 'auth' is used inconsistently, local='auth SHA2-256', remote='auth SHA256'
2022-06-23 17:31:15 Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384, peer certificate: 2048 bit RSA, signature: RSA-SHA1
2022-06-23 17:31:15 [htb] Peer Connection Initiated with [AF_INET]23.19.245.66:1337
2022-06-23 17:31:15 PUSH: Received control message: 'PUSH_REPLY,route 10.10.10.0 255.255.254.0,route 10.129.0.0 255.255.0.0,route-ipv6 dead:beef::/64,tun-ipv6,route-gateway 10.10.14.1,topology subnet,ping 10,ping-restart 120,ifconfig-ipv6 dead:beef:2::1059/64 dead:beef:2::1,ifconfig 10.10.14.91 255.255.254.0,peer-id 40,cipher AES-128-CBC'
2022-06-23 17:31:15 Preserving previous TUN/TAP instance: tun0
2022-06-23 17:31:15 NOTE: Pulled options changed on restart, will need to close and reopen TUN/TAP device.
2022-06-23 17:31:15 net_route_v4_del: 10.10.10.0/23 via 10.10.14.1 dev [NULL] table 0 metric -1
2022-06-23 17:31:15 net_route_v4_del: 10.129.0.0/16 via 10.10.14.1 dev [NULL] table 0 metric -1
2022-06-23 17:31:15 delete_route_ipv6(dead:beef::/64)
2022-06-23 17:31:15 net_route_v6_del: dead:beef::/64 via :: dev tun0 table 0 metric -1
2022-06-23 17:31:15 Closing TUN/TAP interface
2022-06-23 17:31:15 net_addr_v4_del: 10.10.14.91 dev tun0
2022-06-23 17:31:15 net_addr_v6_del: dead:beef:2::1059/64 dev tun0
2022-06-23 17:31:16 net_route_v4_best_gw query: dst 0.0.0.0
2022-06-23 17:31:16 net_route_v4_best_gw result: via 10.0.2.2 dev eth0
2022-06-23 17:31:16 ROUTE_GATEWAY 10.0.2.2/255.255.255.0 IFACE=eth0 HWADDR=08:00:27:37:63:9a
2022-06-23 17:31:16 GDG6: remote_host_ipv6=n/a
2022-06-23 17:31:16 net_route_v6_best_gw query: dst ::
2022-06-23 17:31:16 sitnl_send: rtnl: generic error (-101): Network is unreachable
2022-06-23 17:31:16 ROUTE6: default_gateway=UNDEF
2022-06-23 17:31:16 TUN/TAP device tun0 opened
2022-06-23 17:31:16 net_iface_mtu_set: mtu 1500 for tun0
2022-06-23 17:31:16 net_iface_up: set tun0 up
2022-06-23 17:31:16 net_addr_v4_add: 10.10.14.91/23 dev tun0
2022-06-23 17:31:16 net_iface_mtu_set: mtu 1500 for tun0
2022-06-23 17:31:16 net_iface_up: set tun0 up
2022-06-23 17:31:16 net_addr_v6_add: dead:beef:2::1059/64 dev tun0
2022-06-23 17:31:16 net_route_v4_add: 10.10.10.0/23 via 10.10.14.1 dev [NULL] table 0 metric -1
2022-06-23 17:31:16 net_route_v4_add: 10.129.0.0/16 via 10.10.14.1 dev [NULL] table 0 metric -1
2022-06-23 17:31:16 add_route_ipv6(dead:beef::/64 -> dead:beef:2::1 metric -1) dev tun0
2022-06-23 17:31:16 net_route_v6_add: dead:beef::/64 via :: dev tun0 table 0 metric -1
2022-06-23 17:31:16 OPTIONS IMPORT: timers and/or timeouts modified
2022-06-23 17:31:16 OPTIONS IMPORT: --ifconfig/up options modified
2022-06-23 17:31:16 OPTIONS IMPORT: route options modified
2022-06-23 17:31:16 OPTIONS IMPORT: route-related options modified
2022-06-23 17:31:16 OPTIONS IMPORT: peer-id set
2022-06-23 17:31:16 OPTIONS IMPORT: data channel crypto options modified
2022-06-23 17:31:16 Error: negotiated cipher not allowed - AES-128-CBC not in AES-256-GCM:AES-128-GCM:CHACHA20-POLY1305
2022-06-23 17:31:16 OPTIONS ERROR: failed to import crypto options
2022-06-23 17:31:16 ERROR: Failed to finish option processing
2022-06-23 17:31:16 Failed to open tun/tap interface
2022-06-23 17:31:16 SIGUSR1[soft,process-push-msg-failed] received, process restarting
2022-06-23 17:31:16 Restart pause, 5 second(s)