you need to crack one of the passwords
Enumerate what web server it is and try to find files related to that, and go from there.
thank you but it’s not rocking at all ![]()
Great hint! I must have messed up the LFI but I got it now and got the user own. Thank you! Now to just figure out root.
Also found the hash but I don’t know what to do with it, also tried with hashcat without any success (the hash type seems consistent with the box), I’m not sure if I’m supposed to persist in this way…
I try with another soft.
I’ve found the two hashes, but I’m not sure what to do next. I tried both hashcat and john, but to no avail. Could someone give a hint for how to proceed from here?
How did you create the hash files? Maybe a tool can generate it for you…
Both john and hashcat should work for the hash in conjunction with rockyou.txt
I wasn’t able to crack the admin pass but you can absolutely crack the “manager” pass.
If you feel stuck you can pm me and we could discuss on discord regarding it ![]()
i am here new and i need help
Final step, in case no one else can find it documented, the flag to print to stdout is:
--to stdout
Good luck! DM me for any hints.
Almost everyone I guess.
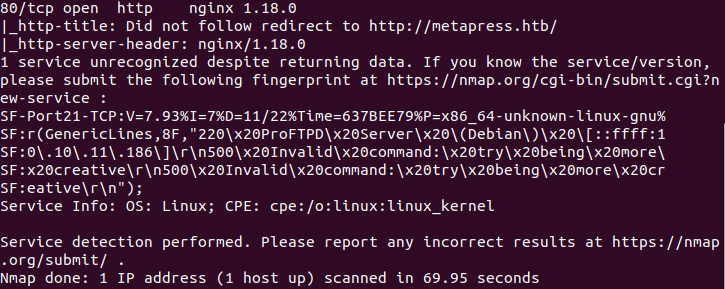
nmap is telling something to you line 2, what could you do to fix it?
I just get timeouts and 504s after editing my hosts file, can anyone just confirm to me if this is expected or not? Have tried resetting.
Hi guys, can somebody help me? I’m using ‘john’ to crack hash, but output is: No password hashes loaded (see FAQ). I have wordlist and file with 2 hashes.
I am having issues with that hash, it keeps giving me a token length exception in hashcat. Am I doing something wrong?
Currently the only plugin that I am finding is bookingpress-appointment-booking However, I am unable to figure out how exactly I should inject the reverse shell. The best I got is to inject it in the nonce parameter and then I get a reply from the website: “Sorry, Your request can not process due to security reason.” If anyone can help, please messsage me. I am also open to discussing on Discord or sth
Interesting box. Feel free to PM on discord if you need help - BroLang#7473
Created a tool to help with this one: https://github.com/BKreisel/CVE-2022-0739
-e ap --plugins-detection aggressive
still no plugins shown =)
(i even updated the famous script) spent hours now, and finally i moved to check for hints and see that was in right direction but doing it wrong? is it happening to other people aswell?