for some reason you need to append the leaked address at the payload i just tried it and it works i don’t know the reason why
I got to the point where I can read and need to pwn leak.
I can call handler and get Bye back. I also understand that there are not enough rop gadgets to call system. I tried ret2csu, but as I understand there are also not enough gadgets for this.
I’m trying to ret2dl, w/ pwntools. But it says that it can’t find any instructions for syscall.
Given the progression of the challenge, it feels like I’m chasing a rabbithole and it should be simpler than that. Can anyone give a hint?
Can someone give a hint on elasticity? The web api seem to accept some chars, e.g. \ or quotes, but I don’t seem to be able to do anything with it.
Internal ports 9200/9300 not responding. Not sure what to do at this point.
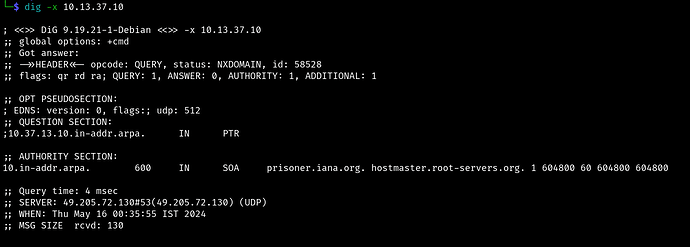
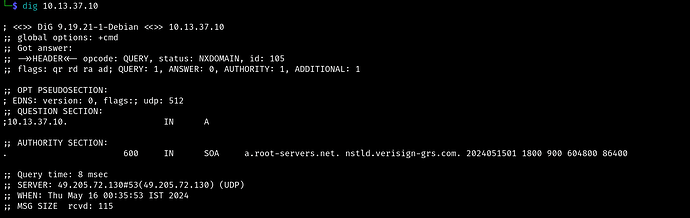
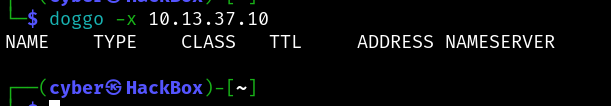
try dig it then you will find some domain name
Could someone please give me a nudge on bypass authentication? I’ve tried everything I know, and all sorts of tools…
Edit: NVM I got it
You have the ip address, you need the domain name - so dig it
Hi everyone, loving it so far ![]()
One thing is troubling me, though. I solved “More Secrets” without solving “Secret Message” first… What did I do wrong? Are we dealing with the same files, or is this first challenge about something completely different, that I missed in my enum? Thanks a lot!
Can smb help me with overflown? Every time I got segm fault
Does someone else have a 504 Gateway Timeout on PHP file? I lost my reverse shell after a Ctrl+C but couldn’t resend my payload because every PHP page send a 504. Root HTML works fine though.
I’m on EU Fortress 1
Could smb help me with elasticity? Internal port resets connection
yeah happened to me just right now after exiting the shell all php files where getting me 504
@everyone here can u reset the machine
Earth to HTB please reset the Jet machine
You did it? I’m already stuck here…
People, tell me about the overflow . RIP under control, but how can I put the reverse shell into 72 bytes? My shellcode is at least 95 bytes?
Can someone help me on Member Manager ?!!
You have to make elf up by yourself
i need your help in digging in and going deeper
i used dig command by using both -x and axfr so far its only showing out of scope domain not sure what to do here is something wrong with the machine. Need your help here.
I am not sure i am also stuck on digging in. I think i have tried everythign can one please help me with this one.
Also please reset eu machine i think something’s not right or i am just stupid because even without vpn and with vpn the result is same
EDIT:
Not sure why machine was not giving me reverse dns lookup at first so saw someone commented on facebook post fqdn from there i added it in my hosts file then axfr worked but still why its not giving any reverse lookup
let me know how you guys got the domain name for this ip
Your dig command is almost right, search on google how to use it. If you don’t find than dm me