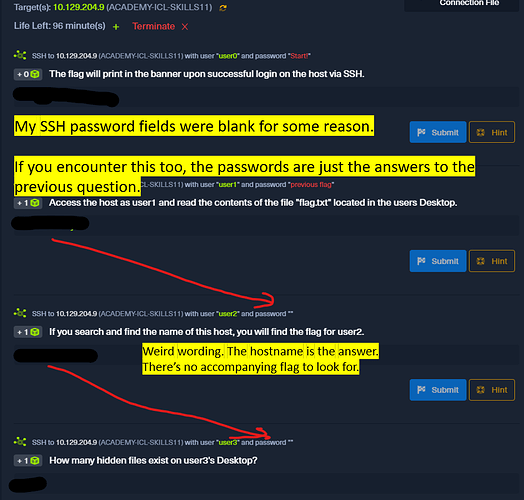
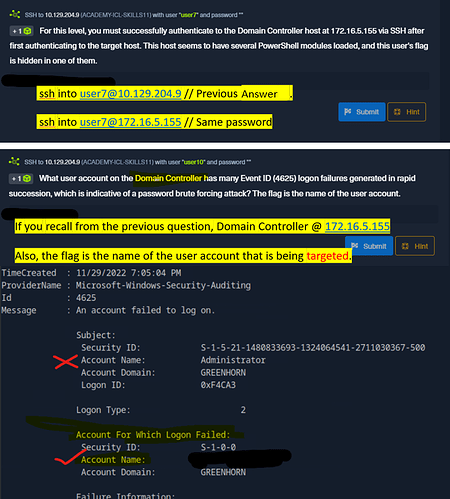
Most of my problems on this section came from the questions themselves. So I wanted to put this here if helps someone else.
Including the questions here so web crawlers can find it. Ignore.
For this level, you must successfully authenticate to the Domain Controller host at 172.16.5.155 via SSH after first authenticating to the target host. This host seems to have several PowerShell modules loaded, and this user’s flag is hidden in one of them.
What user account on the Domain Controller has many Event ID (4625) logon failures generated in rapid succession, which is indicative of a password brute forcing attack? The flag is the name of the user account.