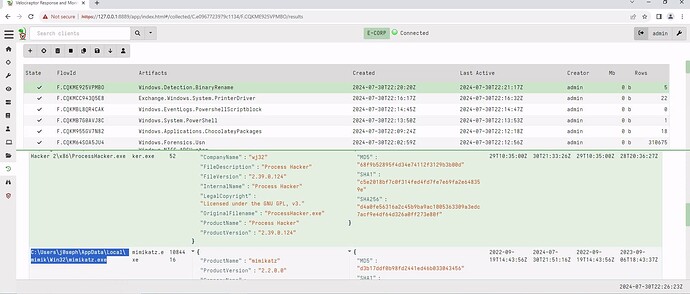
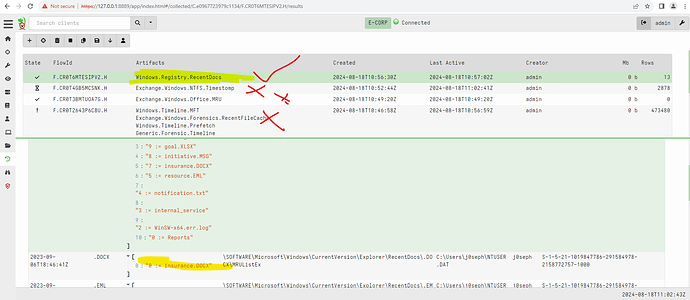
What hunt options should i pick in Velociraptor to get back the data needed? Seems like all the ones that i think make the most sense are not pulling back what’s needed.
Sometimes you have to change the parameters, but the first two questions I got from the files that are already on the machine on Desktop.
I am stuck on
- 2 Determine the registry key used for persistence and enter it as your answer.
and - 2 Determine the folder that contains all Mimikatz-related files and enter the full path as your answer.
I found using Velociraptor to be tedious and didn’t provide me the results I needed to answer the questions. Mind you I was probably just not versed on the tool enough.
I used similar to what bb0rges used. Tools already on the box to answer the questions. Think about other tools used in previous modules to view processes since, if memory serves, two of the questions involve a process.
I solved the task using three collections, not any other data from the target machine. I pulled the results to my local machine and analyzed them there.
The first collection I only used because it was heavily hinted at in the first task, but there are other ways to solve that one. The second one was very generic and often suggested/used throughout the module. I could solve all but one question using that. The third one was extremely specific because I didn’t find the answer in the second collection.
I also noticed that some discussed collections like the memory dump cannot be executed, at least not without pulling some additional executables from the web. The questions can be solved without them.
By the way, I also struggled a bit with the registry key question because I didn’t find the right formatting right away. The answer shall have the full key, but not the value. So the answer format is HKEY...\...\... etc.
Can you please guide me on the 2nd question on hunting the IP address of C2 command and control?
Can you please guide me on the 2nd question on hunting the IP address of C2 command and control?
search for the network connection for the first answer.
Could you please give me a little bit hint… Since I found the key, but still incorrect. I use the full key name until ixxxxxxxxxe , still incorrect…
Nevermind. I found it… Just some kind of wording stuff in the question made me confused.
Sysinternal tools available on the host are pretty helpful. I don’t like these modules, you have to guess or find workarounds instead of being able to simply re-create the steps.
hate this module
I cant seem to find the answers to the last two questions. Any help?
Still need help?
I thought they might have changed the name since I couldn’t find it so I searched in rename.
path: C:\Users\j0seph\AppData\Local\mimik
Cobalt Strike is commonly used for C2. There is a Velociraptor artefact collection for this. Search for ‘cobalt’.
Nice one, I tested a bunch of other execution artefacts too. I also discovered it using Windows Event Logs.
Okay, Done, here are some tips on how to collect datas with velociraptor :
(ignore vad bullshit)
(Think to keyword related to what you look and search an artifact with it)
@hashira , I used the zipped file on the desktop of the VM. then navigated to netstat logs since the target will create a connection with to the C2. Then look for rundll32
Hope this gives you a clue