Dear HTB student.
For this section there is a app called ‘app.js’ and it ask to do the following:
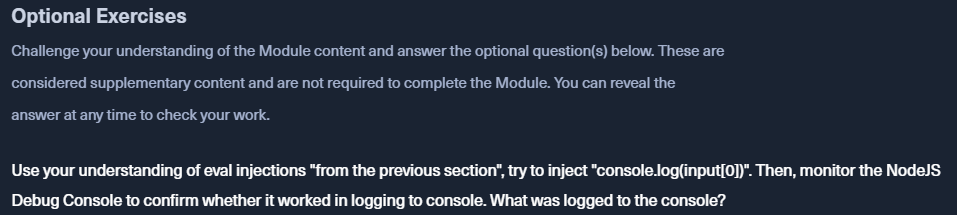
Use your understanding of eval injections “from the previous section”, try to inject “console.log(input[0])”. Then, monitor the NodeJS Debug Console to confirm whether it worked in logging to console. What was logged to the console?
So what I did is als follows:
url = http://localhost:5000/api/service/generate
Ask for admin token:
bc-dev01@ub-devops01:~/Downloads/intro_to_whitebox_pentesting$ curl -s -X POST -H “Content-Type: application/json” -d ‘{“email”: “test@domain”}’
{“token”:“”}
view in ‘jwt.io/’ to confirm the account is admin:
Token decoded:
{
“email”: “test@domain”,
“role”: “admin”,
“iat”: 1729938653,
“exp”: 1730025053
}
Run the following command to hit the error message ‘contains the following invalid characters’
bc-dev01@ub-devops01:~/Downloads/intro_to_whitebox_pentesting$ curl -s -X curl -s -X POST -H “Content-Type: application/json” -H “Authorization: Bearer ” -d ‘{“text”: “;”}’
{“message”:“The input ";" contains the following invalid characters: [;]”}
Then I did changed ‘{“text”: “;”}’ to ‘{“text”: “console.log(input[0])”}’:
curl -s -X POST -H “Content-Type: application/json” -H “Authorization: Bearer ” -d ‘{“text”: “console.log(input[0])”}’
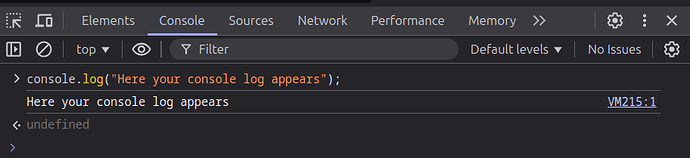
But it generates a QR code, but I am unable to monitor the NodeJS Debug Console. My question is how can I monitor the NodeJS Debug Console?