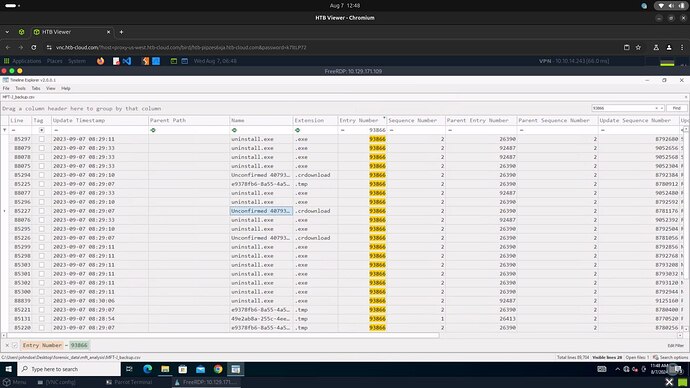
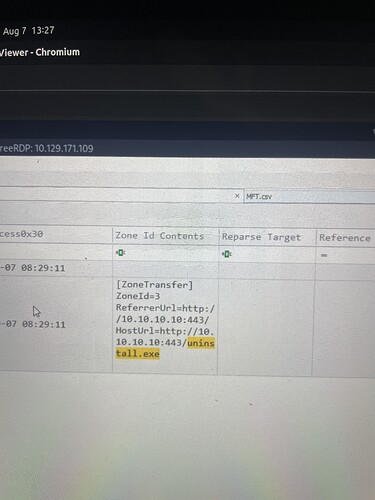
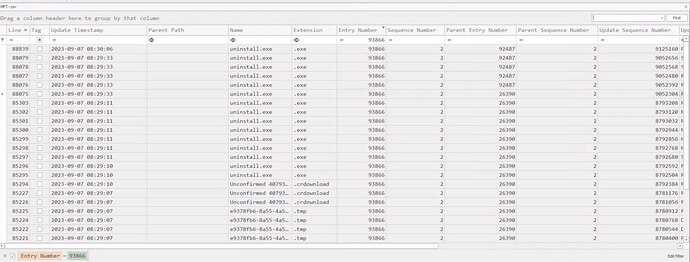
During our examination of the USN Journal within Timeline Explorer, we observed “uninstall.exe”. The attacker subsequently renamed this file. Use Zone.Identifier information to determine its new name and enter it as your answer. any hints on this one
did you solve it bro? i am struck too
no its not ![]()
stuck as well.
parse the MFT open it in time line viewer and look for the zoneID for uninstall.exe, then there is a file name column that will show the original file name.
thanks, i have done that already, i am at last module in soc analyst, appreciate your response
To determine the new name of the “uninstall.exe” file, check the Zone. Identifier information linked to it in Timeline Explorer. Look for any renaming events associated with the file.
Is it useful for you?
You need to define a new file name “uninstall.exe” using the information from Zone.Identifier. It is important to extract this information and continue the analysis without discussing the methods for obtaining it.
saw those clues in the timeline explorer but still can’t find the new name in mft explorer
Managed to solve?
Do you have any idea how to do this?
Well, I got stuck there for a while. Let me help you to get out there:
![]() Make sure to parse to csv the $MFT File, don’t spend a lot of time analyzing $J (USN).
Make sure to parse to csv the $MFT File, don’t spend a lot of time analyzing $J (USN).
Using the Time Explorer, instead of filter by the Entry ID, do it by the file name (uninstall.exe). You will notice a couple of downloads of the file with ZoneIdentifier 3.
From there, just analyze the File Name column, good luck! ![]()
i saw several. like discord.exe, and other but all are wrong. any hint.
Ine other Question, the DRP host is so slow. When I try to click or type some letter it needs more then 3seconds for one click ![]()
someone has an aproch to speed this up?
one day later, works as expected.
solution, i quite simple, read the instruction careful, use the PS script, search with the Timeline Explorer for the uninstall.exe and then have a look to the “FileName” Column
Pls I’m still a bit stuck, I have followed the process in parsing the MTF file
to csv but on loading it to timeline explorer all I can get it’s a zonal id content of ip&name (uninstall.exe) I made my research and found that zonal identifier doesn’t change but on my quest to correlate it with the one that hve same zonal id its where im stuck all the uninstall entries that tally with rename its hidden im analysing the wrong file or what. Pls i need help
Pls I need a hint on the task 3
Examine the contents of the file located at “C:\Users\johndoe\Desktop\forensic_data\APMX64\discord.apmx64” using API Monitor. “discord.exe” performed process injection against another process as well. Identify its name and enter it as your answer.
Hello Cipher,
Wish I had the time or remember exactly how I got the answer ![]()
But, if you follow my steps, in the Time Explorer you should search for somenting like [Hint] “microsoft.windowskits*…”
I hope you find it helpful!
Follow the instructions of the module when API Monitor is used step by step.
Then play with discord.exe in API Monitor.
[HINT] The answer contains “cmd”