Hello mates,
I am writing regarding the Login Brute Forcing module.
I am stuck at the Service Authentication Brute Forcing section.
Question:
Using what you learned in this section, try to brute force the SSH login of the user “b.gates” in the target server shown above. Then try to SSH into the server. You should find a flag in the home dir. What is the content of the flag?
From this section we need to brute force the the SSH login of the user “b.gates”
> TARGET: 134.209.186.158
> PORT: 22
> USER: b.gates
From the NMAP scan i am able to see that the all ports are filtered:
sudo nmap 134.209.186.158 -top-ports=10
Starting Nmap 7.92 ( https://nmap.org ) at 2022-04-02 22:49 BST
Nmap scan report for 134.209.186.158
Host is up (0.0046s latency).
PORT STATE SERVICE
21/tcp filtered ftp
22/tcp filtered ssh
23/tcp filtered telnet
25/tcp filtered smtp
80/tcp filtered http
110/tcp filtered pop3
139/tcp filtered netbios-ssn
443/tcp filtered https
445/tcp filtered microsoft-ds
3389/tcp filtered ms-wbt-server
From the previous section i’ve already create my files: bill.txt and william.txt with cupp and username-anarchy.
$ cupp -i
<SNIP>
$./username-anarchy Bill Gates > bill.txt
But when i am trying to run the hydra, i am getting the following error message:
"**[ERROR] could not connect to ssh://134.209.186.158:22 - Connection refused**"
I even tried to run hydra in a different ways but always i am getting the same error message.
Examples:
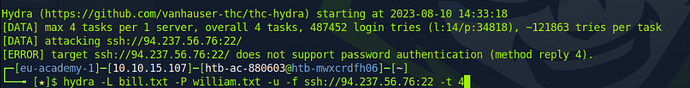
sudo hydra -L bill.txt -P william.txt -u -f ssh://134.209.186.158:22 -t 4
sudo hydra -l b.gates -P william.txt -u -f ssh://134.209.186.158:22 -t 4
I even try to run the hydra with the verbose mode to see if i can get more results when i am trying to run the hydra but the results it’s the same.
$sudo hydra -l b.gates -P /opt/useful/SecLists/Passwords/Leaked-Databases/rockyou.txt -f -f ssh://134.209.186.158:22 -t 4 -vvv
Hydra v9.1 (c) 2020 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2022-04-03 00:15:08
[DATA] max 4 tasks per 1 server, overall 4 tasks, 14344398 login tries (l:1/p:14344398), ~3586100 tries per task
[DATA] attacking ssh://134.209.186.158:22/
[VERBOSE] Resolving addresses ... [VERBOSE] resolving done
[INFO] Testing if password authentication is supported by ssh://[email protected]:22
[ERROR] could not connect to ssh://134.209.186.158:22 - Connection refused
When i am trying to connect to shh, i am getting the same error message: “Connection refused”
$sudo ssh [email protected]
ssh: connect to host 134.209.186.158 port 22: Connection refused
So i’ve decided to check in the ssh log if i can find something that doesn’t allow me to connect to ssh or if there is any additional error message but unfortunately in the ssh log i didn’t find anything just this:
SSH Debug
==========
debug1: Connecting to 134.209.186.158 [134.209.186.158] port 22.
debug1: connect to address 134.209.186.158 port 22: Connection refused
ssh: connect to host 134.209.186.158 port 22: Connection refused
Could you please help and give me advice/tip with this exercise.
- Should i use the generated files from cupp and username-anarchy?
- Is there something wrong with my Virtual Machine( I am using ParrotOS on VmWare)?
- Why even with ssh i am not able to connect to the target?
- Because the ssh port 22 is filtered?
- Or there is something wrong with the firewall?
Thanks in advance
Best Regards,