Guys, did you finished the Attacking Authentication Mechanisms module? I got stuck in the skills assessment, any hint?
I finished recently. my advice is to not overthink. Interact with the page and pay attention with the its response.
Thank you @j0rg3k, I will try play with it
hi bro, still unable to figure it out, any hint for me? i’am getting crazy here
@j0rg3k - I’ve got the token and been able to modify it but I’m not sure where to send it.
I’ve tried to /, /login, and /register and none of those seem to work. I’ve also run gobuster against the target looking for other paths and I haven’t been able to find anything else that’s live.
remember which page asked you the token. you have everything you need. don’t overthink.
@j0rg3k I appreciate the hints but I’m still unable to make any progress.
-I send the required info to /register.
-Login in with the required info at /login and copy the token.
-Use jwt.io to modify isAdmin field to true.
If I send the token to /login or /register, it’s asking for the required info. If I send the info plus the token, it returns yet another token. If I send the token to / it comes back with 404 page not found.
I’m not sure where else I can send the token to. Any other hints would be really helpful.
Thanks
You are on the right track. Remember to validate your jwt token after tampering it. Use the validated token on the page that requested authentication.
@j0rg3k thank you. I’ve made some progress I found the vulnerability and have been able to find the key but I’m still unsure where to send it.
Sending to /login still asks for email/password and sending to / says 404 page not found. You say send it to the page that requested authentication. Is there another page other than /, /login, and /register??
Thank you,
no, those are the three pages
Did you ever figure out how to check it? I’m also stuck getting a 404 error, I pretty much tried, getting the secret, dropping the signature, and editing isAdmin but I am not getting any breakthrough.
Edit: I figured it out, there is something important about the headers when validating the token. ![]()
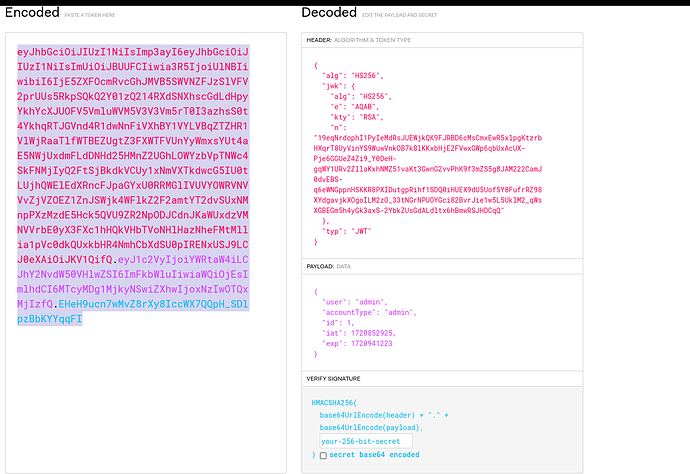
Has anybody figured out how to complete the skill assessment for the new version? After inspecting the request, it very much looks like it is going to be one of the methods taught in the course by generating keys and using a python script, but that doesn’t seem to work for me.
I’ve tried other ways taught in the course, but they haven’t been working for me as well. Any clue? So far everything has been straight forward other than the skill assessment. Really stuck
Just wanna say all the details and methods do come from the course. In my case while testing, I had to run the course’s given python scripts multiple times without changing anything and then suddenly it worked. If you tried a method one time, try it a couple more times and it should work.
How did you do this? ![]() I’ve been running these scripts as well and tried all the possible token attacks. Any tips on changing the payload data? Is changing the existing payload enough?
I’ve been running these scripts as well and tried all the possible token attacks. Any tips on changing the payload data? Is changing the existing payload enough?
Thank you
EDIT: I figured it out. After retrying it worked.
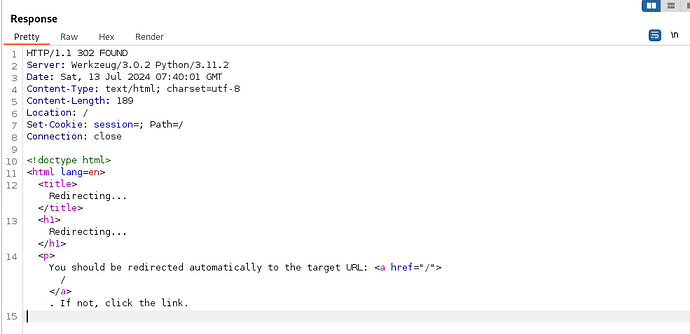
Hello. I am stuck. I got the admin panel. I modify the jwt. i saw there is token that should be consider. I used it. The issue is when checked in the jwt.io it is signed but when i used it i got this as response and it took me back to the home page.
this is the result from jwt.io
Hello. Please, can you help. I am stuck since morning. I tried all possible combination but i think it is going worse.
Hi. Could really use some hint. I’ve tried various combinations of the parameters for the token signing, but nothing seems to work. I’ve went through the course material and no other methods help.
For anyone who is struggling for some time in this. There is an interesting observation in the section which got me hanging for a day or two.
DON’T FORGET TO APPEND A NEW LINE
To add to this, as I was struggling for a long time with this task and the other comments were misleading to me - don’t hang yourself on the one python script given directly in the module if it does not work. What other python scripts could be of any help?
Also a methodology hint - if a method is not working without changing a payload, maybe you should try something else.
This turned out to be a very good exercise, some nice thoughts went into the design, forced me to think. For people who are struggling with this, make sure to thoroughly understand each attack mechanism and be sure each vulnerability type introduced in the module is thoroughly tested. Once you have the clear goal in mind, you’ll figure out a way to get there.