For the first question in the Module “Replicate the DLL hijacking attack described in this section and provide the SHA256 hash of the malicious WININET.dll as your answer. “C:\Tools\Sysmon” and “C:\Tools\Reflective DLLInjection” on the spawned target contain everything you need.” I’m having trouble finding any events in Event Viewer with the Event ID of 7. I’m able to replicate the dll hijacking attack with the pop-up and everything, but there are no Event 7s showing up. It seems like it should be a very easy and straightforward question, but it’s just not working.
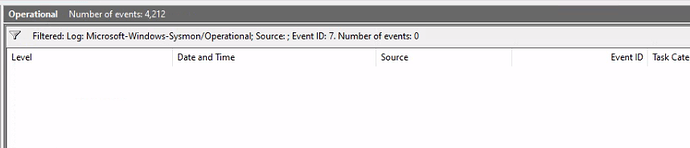
After importing the sysmonconfig-import.xml log file, according to the module, I should see a number of events under “Applications and Services” → “Microsoft” → “Windows” → “Sysmon” with the Event ID of 7. Yet when I go to that exact location and filter for events with the ID of 7, I find nothing. Zero events.
I go and replicate the DLL hijacking attack, shouldn’t this also produce events with the ID of 7? Because when I do it, I get nothing. I get a lot of events showing up, but none of them have the ID of 7. Meanwhile, the Module walkthrough shows events with an ID of 7 showing up. I follow the same steps exactly the same and yet my result is different. I am so confused.
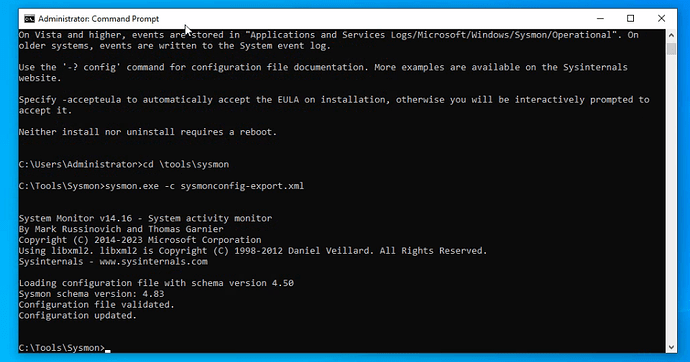
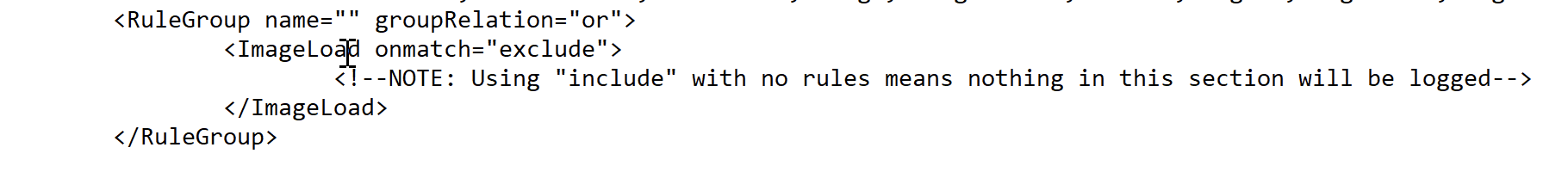
Did you replaced include to exclude in the sysmonconfig-export.xml before executing the sysmon.exe -c sysmonconfig-export.xml ?
For the first question in the Module “Replicate the DLL hijacking attack described in this section and provide the SHA256 hash of the malicious WININET.dll as your answer. “C:\Tools\Sysmon” and “C:\Tools\Reflective DLLInjection” on the spawned target contain everything you need.” I’m having trouble finding any events in Event Viewer with the Event ID of 7. I’m able to replicate the dll hijacking attack with the pop-up and everything, but there are no Event 7s showing up. It seems like it should be a very easy and straightforward question, but it’s just not working
After importing the sysmonconfig-import.xml log file, according to the module, I should see a number of events under “Applications and Services” → “Microsoft” → “Windows” → “Sysmon” with the Event ID of 7. Yet when I go to that exact location and filter for events with the ID of 7, I find nothing. Zero events.
I go and replicate the DLL hijacking attack, shouldn’t this also produce events with the ID of 7? Because when I do it, I get nothing. I get a lot of events showing up, but none of them have the ID of 7. Meanwhile, the Module walkthrough shows events with an ID of 7 showing up. I follow the same steps exactly the same and yet my result is different. I am so confused.
I ran the config file without modification first. I think you have to restart the service if you make changes after the first run… Nothing was showing up when filtering for ID 7 for me either. After running the proper config, restarting the service and refreshing the event view. They started to show up.
From the sysmonconfig-export.xml file, you need to open with notepad and change the ‘include’ to ‘exclude’
And afterward execute it again in command line and you will see the event id 7
did you have problem with permission, I can’t move calc.exe in the pwnbox they gave me
I am having the same issue =(
how did you manage to move the calc.exe to the documents folder? I am having issue doing that
Unless copy pasting Calc.exe works
This works thank you!
Let’s attempt the hijack using “calc.exe” and “WININET.dll” as an example. To simplify the process, we can utilize Stephen Fewer’s “hello world” reflective DLL. It should be noted that DLL hijacking does not require reflective DLLs.
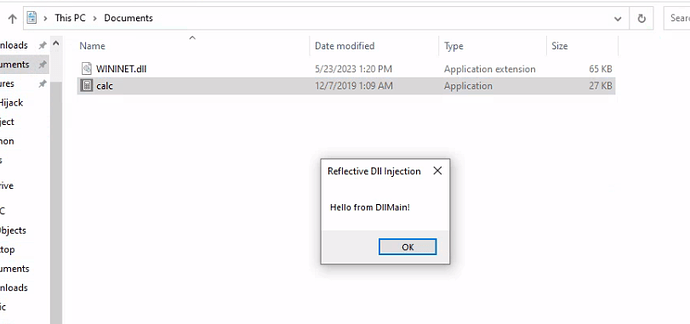
By following the required steps, which involve renaming reflective_dll.x64.dll to WININET.dll, moving calc.exe from C:\Windows\System32 along with WININET.dll to a writable directory (such as the Desktop folder), and executing calc.exe, we achieve success. Instead of the Calculator application, a MessageBox is displayed.
Please how do i get the reflective dll to the target machine
Bro, I’m having the same issue, did you solved? How?
Na’, I already solved, here is the answer: 51F2305DCF385056C68F7CCF5B1B3B9304865CEF1257947D4AD6EF5FAD2E3B13
Ok so how did you solve it?
Would really appreciate help with the first question. More so with this part of the process:
-
Let’s attempt the hijack using “calc.exe” and “WININET.dll” as an example. To simplify the process, we can utilize Stephen Fewer’s “hello world” reflective DLL. It should be noted that DLL hijacking does not require reflective DLLs.
-
By following the required steps, which involve renaming
reflective_dll.x64.dlltoWININET.dll, movingcalc.exefromC:\Windows\System32along withWININET.dllto a writable directory (such as theDesktopfolder), and executingcalc.exe, we achieve success. Instead of the Calculator application, a MessageBox is displayed.
I don’t understand the “step by step” process. I have no idea what to do. I’m doing this as a recommendation project from Unixguy. I cannot figure this out for the life of me.