Here, my hints once I found the flag
1- Use one of the previous SOAP request scripts and adapt it
2- You will need to use single quote for SQLi so keep that in mind while you write your script
3- As @onthesauce said before, if nothing happen when you execute it means that it’s working so start to think about the SQLi payload.
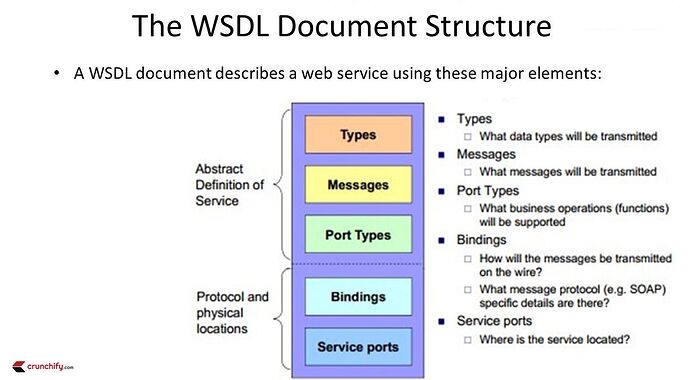
4- Web Service Hacking | SOAP and WSDL you can find some great info here.
Anyone have any tips on ho you found the flag? Having issues
check out @onthesauce write up above. He lays it out pretty clearly.
some other tips i can offer:
- the lesson doesnt do a very good job at explaining how to interact with SOAP APIs in my opinion, but think of which method could be exploited for a SQL injection, then craft the right request for that method
- SOAP APIs require you to talk to them in their convoluted language (as opposed to REST APIs which take in JSON) - get that request under your belt
- the site wont respond even if the request has the required arguments in it (which is pretty annoying). Instead, it will respond to a request with the required arguments AND a malicious payload. I guess they did this to prevent automated scanners like SQLmap from making it too easy?
- extra tip: if you want to use SQL map, learn about tweaking different injection techniques…one of these techniques works like the charm, the other ones run into that non responsive state
Can someone give me a hand to find the flag. I’m stuck with this skill. Thanks
DM me
What’s up friend, of course you can solve it, do you need help?
This one was confusing at first but the hints here are definitely enough. The only thing I’ll add is, I thought once I found and sqli point I thought I was supposed to enumerate a database to get a password, but just submitting a different sqli payload gets you the flag in the response.
This challenge is very good, it reinforces my understanding of SOAP attacks. Tips: You only need to understand the “RCE by soap” part and change it to SQLi to complete the challenge.
The quote in step 4 reminds me. Thank you!
Hey mate need your help…
I did the injection in the username with admin' OR 1=1-- and got the following record: id>1KaleenaUndrill[email protected]kundrill05403b63f6e34ac7baf9b45b12ebcdef8" However if I do “admin' SELECT * FROM users WHERE username = admin OR 1=1--” I get the following error message: “b'SqliteError: near "SELECT": syntax error\n at Database.prepare ...”
Any hint/suggestion on how to tackle this?
Thanks in advance!
I crafted the ExecuteCommand request to Login request and placed a simple sqli in the username field and ended up getting the record of one “kundrill0” but was not able to enumerate any fruther … any hint/suggestion?
I don’t remember the specific payload I used, but it’s a simple sqli where you’re already trying. The flag should return in the webpage response.
I originally kept trying thinking I had to log in or I had to enumerate the database with sqlmap, but the flag will just show with the correct payload.
Hey dude, the first payload you had above looks pretty good. DM me the SOAP request you have crafted and I will help you further.
-onthesauce
sure mate, will do right away.
Actually I am wrong here, that payload isn’t quite right. (Putting this here so others don’t waste their time thinking its a valid payload haha.)
It just needs a little tweaking.
Takeaway:
This module is the worst kind of explanation in entire academy, I had to follow many guidelines and research a lot to understand the basics on SOAP and WSDL terminology.
- WSDL needs to be read from bottom to top
Solution:
Remember there are always LIMT and OFFST functions in SQL that migth be helpful ![]()
Thanx for the link… After reading I was able to craft a simpler SQL query.
For people who struggle… There is one query that you are not required to enumerate the whole table.
No need to write or mod a script.
Since the password format is already provided by the module, you can craft a query to retrieve the user with that password format. I would suggesting reading the link provided by @q3alique.
Thanks for putting all that together, you saved me hours.
There is only 24 hours in a day and I don’t have time to spend half of it on a module.
Whoever wrote that module did a sloppy job.
Thank you. Much appreciated.