I’m stuck in Hunt 3 from last 2 days, Any hint?
PwrVe is the correct answer
for those who still struggling to get answer for P----V— question, just try filtering with powershell.file.script_block_text and use the value as P(star)V(star). In place of (star) just use star symbol.This will highlight all the strings with P and V. You dont need to expand and read, just scroll through all the highlighted strings and answer will be there. There are lot of strings actually that doesnt make any sense, just go for those that you can form a word or readable spelling. Good luck, and if you cant find let me know
I tried this but step 3 didnt work for me. I simply get no logs when I type in that filter in the search bar
actually nvm bro found it thank you so much. legend
hey peeps,
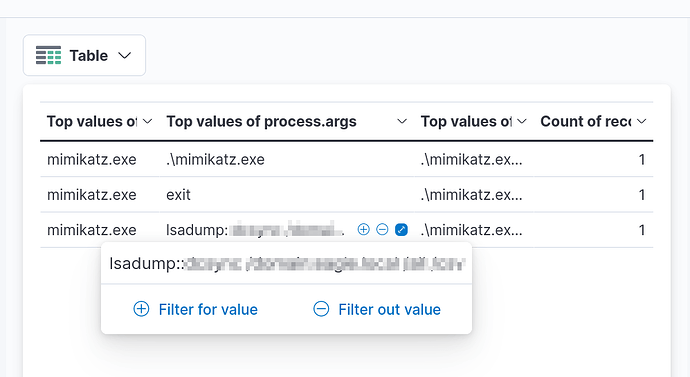
Stuxbot uploaded and executed mimikatz. Provide the process arguments (what is after .\mimikatz.exe, …) as your answer.
I seem to have a slight challenge with this question. I got the mimikatz execution, but the arguments I entered all seem not to be correct. Is there something I’m missing out, please?
ok man, it has to be 100% perfectly copied otherwise it will not be correct, my answer is kinda close to it but not 100, look stuff like .arg
“Stuxbot uploaded and executed mimikatz. Provide the process arguments (what is after .\mimikatz.exe, …) as your answer.”
Some hint?
In .arg field, take everything behind the comma, no space at the begin or the end.
I sent you a message explaining my problem
The ‘process.args’ and ‘process.command_line’ in the event are slightly different - ‘process.args’ doesn’t have double apostrophes, and that’s what it accepted as the correct answer.
I pulled the logs with process name powershell and the initial host name. the used the filters to show only the powershell.file.script_block_text events. added that same field and powershell sequence field and as i was going through the sequence numbers saw it but more accidentally than knowing what I am doing
Use powershell.file.script_block_text:P(star)V(star) As your filter and also choose it as field on the table,also add event code 4104 as filter
Answer:Po*Vi
Anybody got a clue for Hunt 2?
I feel like I have entered every single registry.value into the answer field based on the hint query provided. The article link provided doesn’t seem to help either.
The post shared earlier unfortunately no longer exists.
Nevermind… I got it.
I’ve been doing the Hunt 3 for skills assessment. I was able to get the answer but haven’t got the steps to get there. If someone could explain that would help a lot.
I started off by running process.name:powershell.exe and event.code:4648 on the filter to find out the process that would attempt at logging in on an account by explicitly specifying the account credentials. From there I was able to get that the powershell was used to remotely access the ‘administrator’ account in the ‘DC1.eagle.local’ host, by the ‘bob’ account that’s using the ‘WS001.eagle.local’ host. That was all I was able to get from the ‘message’. I tried checking all logs with the ‘bob’ username that was using the WS001.eagle.local but couldn’t find any links so far.
I was able to get the solution by using ‘event.code:4104’ and ‘powershell.file.script_block_text:*’ based on the previous and trialed all the winlog.user.name.